OpenTelemetry
Receive logs, metrics, and traces from OpenTelemetry clients over the OpenTelemetry Protocol (OTLP/gRPC).
Prerequisites
If you want to enable TLS encryption for this connector to encrypt the communication with the sources, you’ll need to set appropriate keys and certificates.
CAUTION:
Copy the keys and certificates to AxoRouter before starting to configure the connector. Otherwise, you won’t be able to make configuration changes that require reloading the AxoRouter service, including starting log tapping or flow tapping.Note the following points:
-
Keys and certificates must be in PEM format.
-
If the file contains a certificate chain, the file must begin with the certificate of the host, followed by the CA certificate that signed the certificate of the host, and any other signing CAs in order.
-
You must manually copy these files to their place on the AxoRouter host, currently you can’t distribute them from AxoConsole.
The files must be readable by the
axorouterservice. -
The recommended path for certificates is under
/etc/axorouter/user-config/(for example,/etc/axorouter/user-config/tls-key.pem). (If you need to use a different path, you have to append an option like-v /your/path:/your/pathto theAXOROUTER_PODMAN_ARGSvariable of/etc/axorouter/container.env.) -
When referring to the key or certificate during when configuring the connector, use absolute paths (for example,
/etc/axorouter/user-config/tls-key.pem).
Add new OpenTelemetry connector
To add a new connector to an AxoRouter host, complete the following steps:
-
Select Routers > Connector Rules > Add Rule. (Alternatively, you can select Add Connector > Create a connector rule on the Connectors page of an AxoRouter host.)
-
Select OpenTelemetry.
-
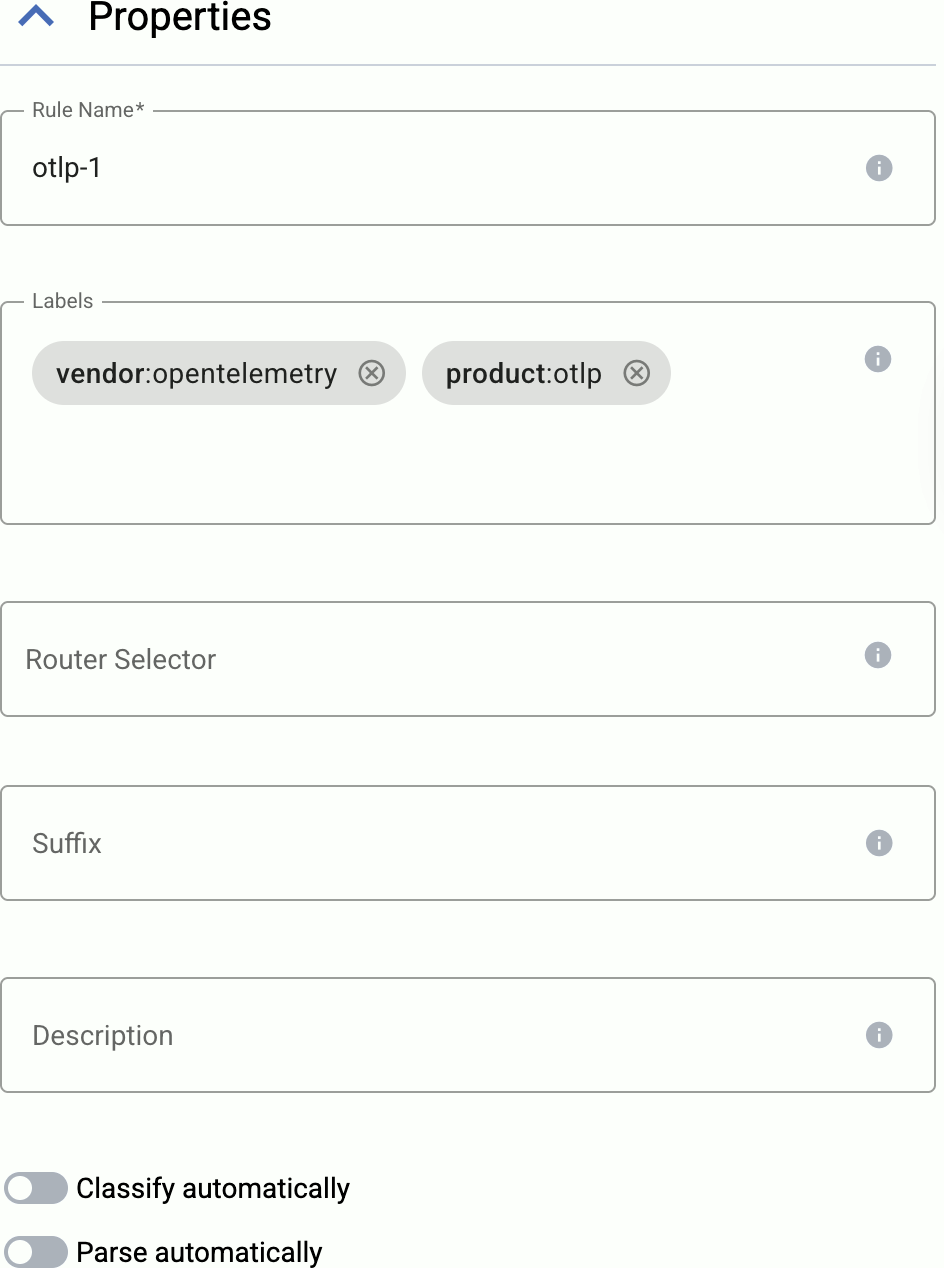
Configure the connector rule.
-
Enter a name for the connector rule into the Rule Name field.
-
(Optional) Add labels to the connector rule. You will be able to use these labels in Flow Processing steps, for example, in the Query field of Select Messages steps. For details about the message schema and the related connector-specific fields, see the
meta.connectorobject. -
Set the Router Selector for the connector rule. The selector determines which AxoRouter instances will have a connector based on this connector rule.
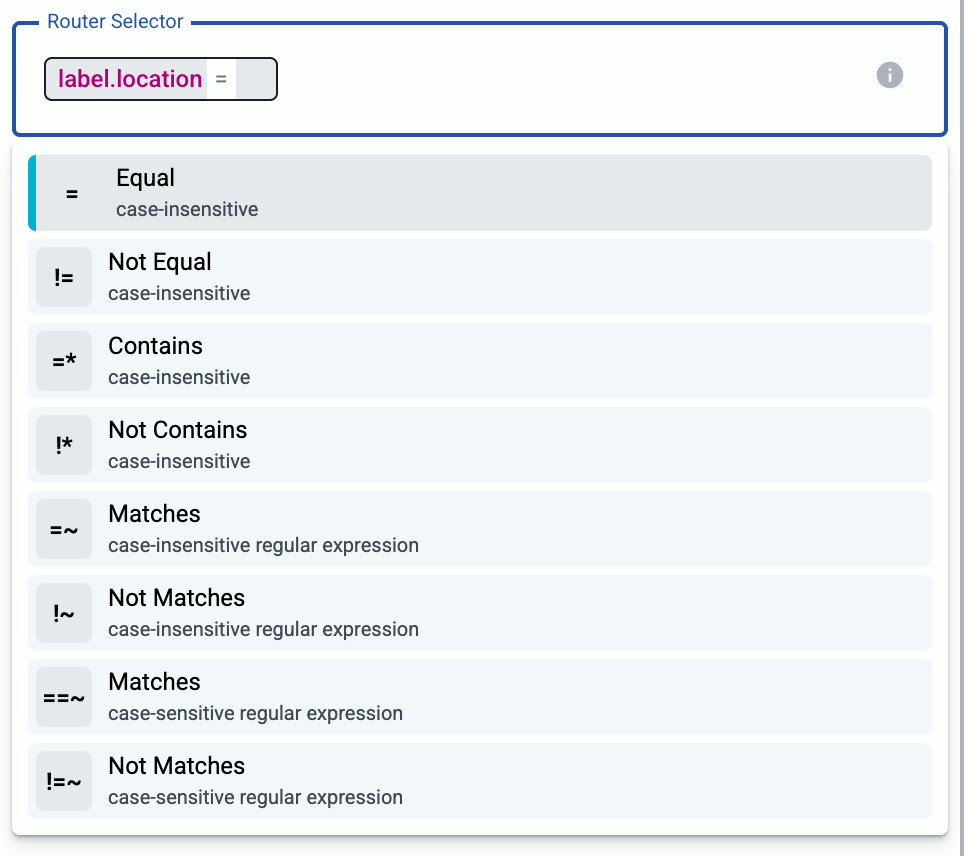
You can use any labels and metadata of the AxoRouter hosts in the Router selectors, for example, the hostname of the AxoRouter, or any custom labels.
- If you leave the Router Selector field empty, the selector will match every AxoRouter instance.
- To select only a specific AxoRouter instance, set the
namefield to the name of the instance as selector. For example,name = my-axorouter. - If you set multiple fields in the selector, the selector will match only AxoRouter instances that match all elements of the selector. (There in an AND relationship between the fields.)
-
(Optional) Enter a Suffix for the connector rule. This suffix will be used in the name of the connector instances created on the AxoRouter hosts. For example, if the name of a matching AxoRouter instance is “my-axorouter”, and the suffix of the rule is “otlp-rule”, the connector created for the AxoRouter will be named “my-axorouter-otlp-rule”.
If the Suffix field is empty, the name of the connector rule is used instead.
-
(Optional) Enter a description for the rule.
-
If needed, enable the Classify and Parse preprocessing steps so AxoRouter automatically identifies and parses messages sent by supported data sources. If your source is not listed, contact us.
Enabling these options processes all data received by the connectors created based on this connector rule. If you want to apply classification and parsing more selectively, you can use the Classify and Parse processing steps in your Flows.
Note that the Parse processing step requires Classify to be enabled. Parsing automatically parses the data from the content of the message, and replaces the message content (the
log.bodyfield in the internal message schema) with the structured information. -
(Optional) If needed, you can add other preprocessing steps to the connector rule. You can use the same processing steps as in flows. These can be useful if you use a dedicated connector rule to fix or annotate data coming from some specific sources.
-
-
If needed, configure the port number where you want to receive data.
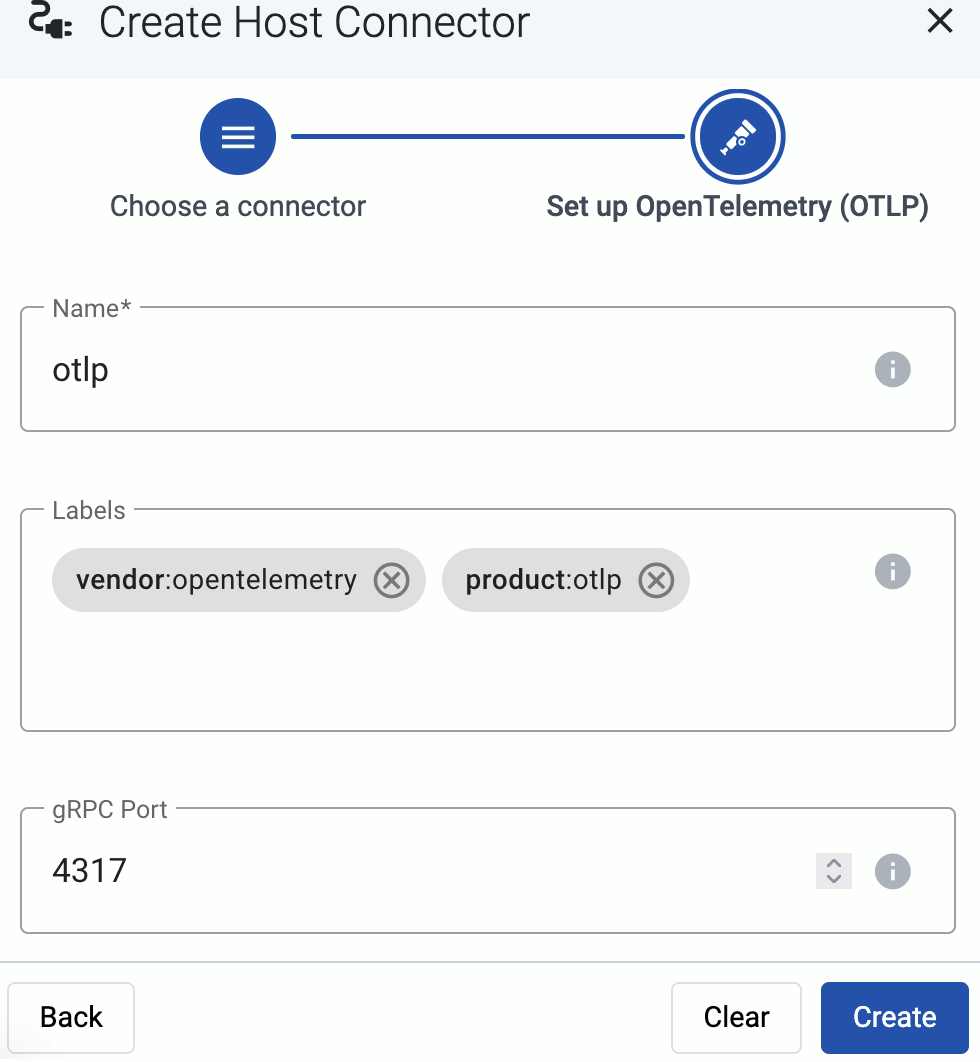
-
Configure TLS settings for the connector.
-
Select Server TLS.
-
Set the path to the key and certificates.
When using TLS, set the paths for the certificates and keys used for the TLS-encrypted communication with the clients. For details, see Prerequisites.
- Server certificate path: The certificate that AxoRouter shows to the clients.
- Server private key path: The private key of the server certificate.
- CA certificate path: The CA certificate that AxoRouter uses to verify the certificate of the sender if Verify peer certificate is enabled.
-
To require the certificates of the clients to be valid, select Verify client certificate. When selected, the certificate of the client cannot be self-signed, and its common name must match the hostname or IP address of the client.
-
-
(Optional) Adjust the flow-control related options if needed.
-
Initial log window size: The size (number of messages) of the initial window used in flow control. For details, see the AxoSyslog documentation.
If you change the value of Initial log window size, the change will affect only new connections, the Initial log window size of already established connections will not change. To apply the new Initial log window size value to every connection, restart the
axorouter.serviceservice on the Services page of the matching AxoRouters. A simple configuration reload is NOT sufficient.If the connector rule is receiving data using the UDP protocol, always restart the
axorouter.serviceservice on the Services page of the matching AxoRouters.
- Log fetch limit: The maximum number of messages fetched from a source during a single poll loop. For details, see the AxoSyslog documentation.
-
-
Select Add.
Axoflow automatically creates connectors on the AxoRouter hosts that match the Router Selector.
Make sure to enable the ports you’ve configured in the connector on the firewall of the AxoRouter host, and on other firewalls between the AxoRouter host and your data sources.
Labels
| Analytics label | Message field | value |
|---|---|---|
connector.type |
meta.connector.type |
otlp |
connector.name |
meta.connector.name |
The Name of the connector |
connector.port |
meta.connector.port |
The port number where the connector receives data |
You can use the labels as:
- Filter labels on the Analytics page,
- in the Filter By Label field during log tapping.
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.