This is the multi-page printable view of this section.
Click here to print.
Return to the regular view of this page.
Vendors
Prerequisites
Steps
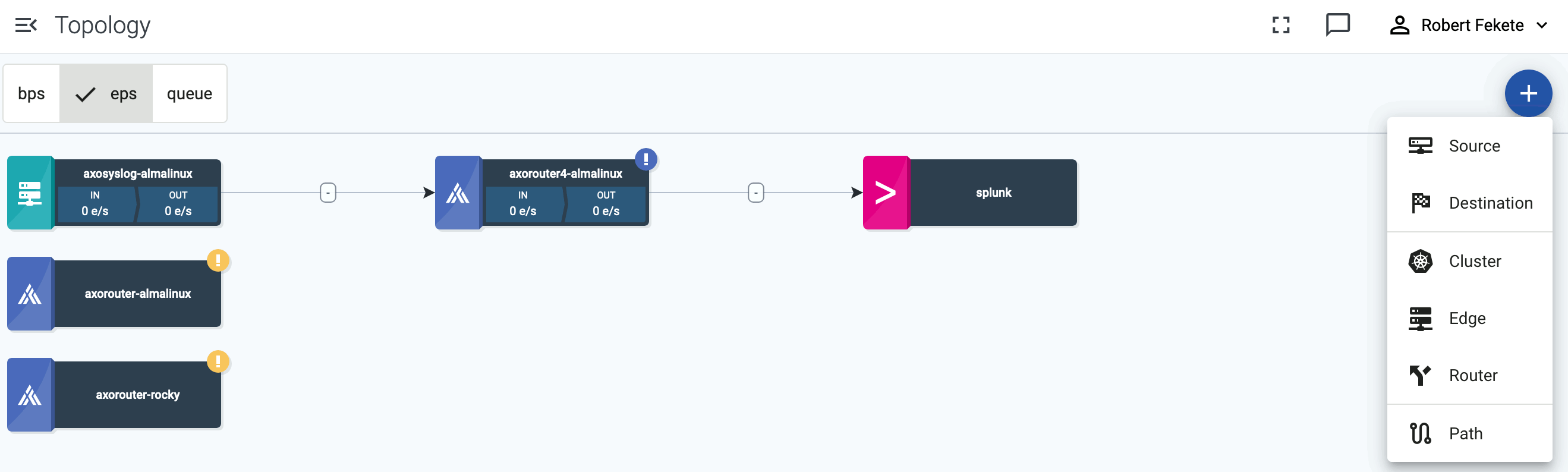
To onboard a source that is specifically supported by Axoflow, complete the following steps. Onboarding allows you to collect metrics about the host, and display the host on the Topology page.
-
Open the AxoConsole.
-
Select Topology.
-
Select Add Item > Source.
-
If the source is already sending logs to an AxoRouter instance that is registered in the AxoConsole, select Detected, then select the source.
Otherwise, select the type of the source you want to onboard, and follow the on-screen instructions.

-
Connect the source to the destination or AxoRouter instance it’s sending logs to. If you’ve added the source from the Detected list, you can skip this step, as the path is created automatically.
-
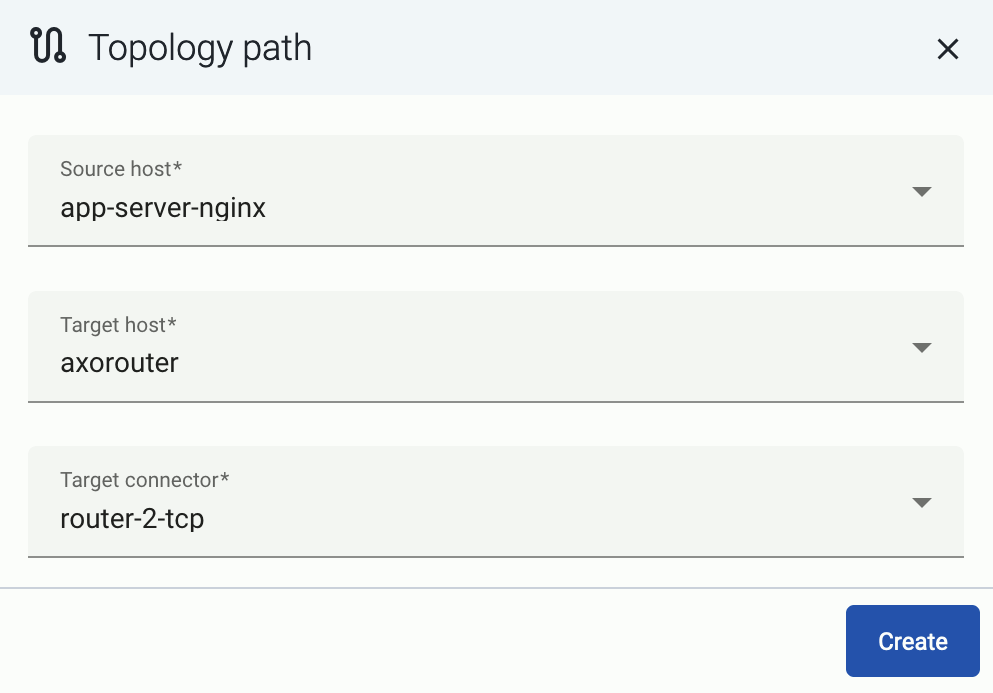
Select Topology > Add Item > Path.

-
Select your data source in the Source host field.
-
Select the target router or aggregator this source is sending its data to in the Target host field, for example, axorouter.
-
Select the Target connector. The connector determines how the destination receives the data (for example, using which protocol or port).
-
Select Add. The new path appears on the Topology page.
-
Configure the source to send logs to an AxoRouter instance. Specific instructions regarding individual vendors are listed below, along with default metadata (labels) and specific metadata for Splunk.
Note
Unless instructed otherwise, configure your source to send the logs to the Syslog connector of AxoRouter, using the appropriate port. Use RFC5424 if the source supports it.
- 514 UDP and TCP for RFC3164 (BSD-syslog) and RFC5424 (IETF-syslog) formatted traffic. AxoRouter automatically recognizes and handles both formats.
- 601 TCP for RFC5424 (IETF-syslog) and RFC3164 (BSD-syslog) formatted traffic. AxoRouter automatically recognizes and handles both formats.
- 6514 TCP for TLS-encrypted syslog traffic.
1 - A10 Networks
1.1 - vThunder
vThunder:
Delivers application load balancing, traffic management, and DDoS protection for enterprise networks.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
a10networks:vThunder:cef |
a10networks:vThunder |
netwaf |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: A10_LOAD_BALANCER.
2 - Amazon
2.1 - CloudWatch
CloudWatch:
Monitors AWS resources and applications by collecting metrics, logs, and setting alarms.
Axoflow can collect data from your Amazon CloudWatch. At a high level, the process looks like this:
- Deploy an Axoflow Cloud Connector that will collect the data from your CloudWatch. Axoflow Cloud Connector is a simple container that you can deploy into AWS, another cloud provider, or on-prem.
- The connector forwards the collected data to the OpenTelemetry connector of an AxoRouter instance. This AxoRouter can be deployed within AWS, another cloud provider, or on-prem.
- Configure a Flow on AxoConsole that processes and routes the collected data to your destination (for example, Splunk or another SIEM).

Prerequisites
Steps
To collect data from AWS CloudWatch, complete the following steps.
-
Deploy an Axoflow Cloud Connector.
-
Access the Kubernetes node or virtual machine where you want to deploy Axoflow Cloud Connector.
-
Set the following environment variable to the IP address of the AxoRouter where you want to forward the data from CloudWatch. This IP address must be accessible from the connector. You can find the IP address of AxoRouter on the Routers > AxoRouter > Overview page.
export AXOROUTER_ENDPOINT=<AxoRouter-IP-address>
-
(Optional) By default, the connector stores positional and other persistence-related data in the /etc/axoflow-otel-collector/storage directory. In case you want to use a different directory, set the STORAGE_DIRECTORY environment variable.
-
Run the following command to generate a UUID for the connector. AxoConsole will use this ID to identify the connector.
UUID_FULL=$(uuidgen 2>/dev/null || cat /proc/sys/kernel/random/uuid 2>/dev/null || python3 -c "import uuid; print(uuid.uuid4())")
export AXOCLOUDCONNECTOR_DEVICE_ID=$(echo "$UUID_FULL" | cut -d'-' -f1)
-
Set TLS encryption to secure the communication between Axoflow Cloud Connector and AxoRouter.
Configure the TLS-related settings of Axoflow Cloud Connector using the following environment variables.
| Variable |
Required |
Default |
Description |
AXOROUTER_TLS_INSECURE |
No |
false |
Disables TLS encryption if set to true |
AXOROUTER_TLS_INCLUDE_SYSTEM_CA_CERTS_POOL |
No |
false |
Set to true to use the system CA certificates |
AXOROUTER_TLS_CA_FILE |
No |
- |
Path to the CA certificate file used to validate the certificate of AxoRouter |
AXOROUTER_TLS_CA_PEM |
No |
- |
PEM-encoded CA certificate |
AXOROUTER_TLS_INSECURE_SKIP_VERIFY |
No |
false |
Set to true to disable TLS certificate verification of AxoRouter |
AXOROUTER_TLS_CERT_FILE |
No |
- |
Path to the certificate file of Axoflow Cloud Connector |
AXOROUTER_TLS_CERT_PEM |
No |
- |
PEM-encoded client certificate |
AXOROUTER_TLS_KEY_FILE |
No |
- |
Path to the client private key file of Axoflow Cloud Connector |
AXOROUTER_TLS_KEY_PEM |
No |
- |
PEM-encoded client private key |
AXOROUTER_TLS_MIN_VERSION |
No |
1.2 |
Minimum TLS version to use |
AXOROUTER_TLS_MAX_VERSION |
No |
- |
Maximum TLS version to use |
Note
You’ll have to include the TLS-related environment variables you set in the docker command used to deploy Axoflow Cloud Connector.
-
Configure the authentication that the Axoflow Cloud Connector will use to access CloudWatch. Set the environment variables for the authentication method you want to use.
-
AWS Profile with a configuration file: Set the region and the AWS_PROFILE
export AWS_PROFILE=""
export AWS_REGION=""
-
AWS Credentials: To use AWS access keys, set an access key and a matching secret.
export AWS_ACCESS_KEY_ID=""
export AWS_SECRET_ACCESS_KEY=""
export AWS_REGION=""
-
EC2 instance profile:
-
Deploy the Axoflow Cloud Connector. The exact command depends on the authentication method and the TLS settings you want to configure.
-
AWS Profile with a configuration file: Set the region and the AWS_PROFILE. Also, pass the TLS-related settings you’ve set earlier.
docker run --rm \
-v "${STORAGE_DIRECTORY}":"${STORAGE_DIRECTORY}" \
-e AWS_PROFILE="${AWS_PROFILE}" \
-e AWS_REGION="${AWS_REGION}" \
-e AWS_SDK_LOAD_CONFIG=1 \
-e AXOROUTER_ENDPOINT="${AXOROUTER_ENDPOINT}" \
-e STORAGE_DIRECTORY="${STORAGE_DIRECTORY}" \
-e AXOCLOUDCONNECTOR_DEVICE_ID="${AXOCLOUDCONNECTOR_DEVICE_ID}" \
-e <TlS-related-environment-variable>="${<TlS-related-environment-variable>}" \
-v "${HOME}/.aws:/cloudconnectors/.aws:ro" \
ghcr.io/axoflow/axocloudconnectors:latest
-
AWS Credentials: To use AWS access keys, set an access key and a matching secret. Also, pass the TLS-related settings you’ve set earlier.
docker run --rm \
-v "${STORAGE_DIRECTORY}":"${STORAGE_DIRECTORY}" \
-e AWS_ACCESS_KEY_ID="${AWS_ACCESS_KEY_ID}" \
-e AWS_SECRET_ACCESS_KEY="${AWS_SECRET_ACCESS_KEY}" \
-e AWS_REGION="${AWS_REGION}" \
-e AXOROUTER_ENDPOINT="${AXOROUTER_ENDPOINT}" \
-e AXOCLOUDCONNECTOR_DEVICE_ID="${AXOCLOUDCONNECTOR_DEVICE_ID}" \
-e <TlS-related-environment-variable>="${<TlS-related-environment-variable>}" \
-e STORAGE_DIRECTORY="${STORAGE_DIRECTORY}" \
ghcr.io/axoflow/axocloudconnectors:latest
-
EC2 instance profile: Also, pass the TLS-related settings you’ve set earlier.
docker run --rm \
-v "${STORAGE_DIRECTORY}":"${STORAGE_DIRECTORY}" \
-e AWS_REGION="${AWS_REGION}" \
-e AXOROUTER_ENDPOINT="${AXOROUTER_ENDPOINT}" \
-e AXOCLOUDCONNECTOR_DEVICE_ID="${AXOCLOUDCONNECTOR_DEVICE_ID}" \
-e <TlS-related-environment-variable>="${<TlS-related-environment-variable>}" \
-e STORAGE_DIRECTORY="${STORAGE_DIRECTORY}" \
ghcr.io/axoflow/axocloudconnectors:latest
The Axoflow Cloud Connector starts forwarding logs to the AxoRouter instance.
-
Add the appliance to AxoConsole.
- Open the AxoConsole and select Topology.
- Select Add Item > Source.
- Select AWS CloudWatch.
- Enter the IP address and the FQDN of the Axoflow Cloud Connector instance.
- Select Add.
-
Create a Flow to route the data from the AxoRouter instance to a destination. You can use the Labels of this source to select messages from this source.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
aws:cloudwatchlogs |
aws-activity |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: AWS_CLOUDWATCH.
3 - Axoflow
3.1 - AxoSyslog
AxoSyslog:
High-performance, configurable syslog service for collecting, processing, and forwarding log data.
Configure AxoSyslog to send data to an OpenTelemetry Connector of an AxoRouter instance using its syslog-ng-otlp destination. If that’s not possible for some reason, use the syslog-ng destination with a Syslog Connector of an AxoRouter instance.
For the best integration of your AxoSyslog instances with AxoConsole, see AxoSyslog.
Labels
Enable classification and parsing in the connector rule that receives data from this source. Axoflow will identify the messages and add labels accordingly.
4 - Broadcom
4.1 - Edge Secure Web Gateway (Edge SWG)
Edge Secure Web Gateway (Edge SWG):
Secures web traffic through policy enforcement, SSL inspection, and real-time threat protection.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
bluecoat:proxysg:access:syslog |
netops |
bluecoat:proxysg:access:kv |
netproxy |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: BROADCOM_EDGE_SWG.
Earlier name/vendor
- Blue Coat Proxy
- Blue Coat ProxySG
- Symantec ProxySG
- Symantec Edge Secure Web Gateway
- Symantec Edge SWG
4.2 - ESX
ESX:
The primary function of ESX is to partition a physical server into multiple virtual machines (VMs), allowing different operating systems to run simultaneously and improving hardware utilization.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label |
Message field |
value |
vendor |
meta.vendor |
broadcom |
product |
meta.product |
esx |
service |
meta.service.name |
vmk, lsud, vsan, iofiltervpd, hostd, cmmdstimemachine, vmware, vpxa, eam, rhttpproxy, sdrsInjector, fdm, esxupdate, healthd, ConfigStore, kmxa, crx-cli, backup.sh, configStoreBackup, Host, vmauthd, localcli, watchdog-vsanperfsvc, watchdog-iofiltervpd, apiForwarder, tmpwatch, .etc.init.d.vsanmgmtd, ComplianceManager, hostprofiletrace, vobd, ucs-tool-esxi-inv, usbarb, auto-backup, cmmdsTimeMachineDump |
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| source |
sourcetype |
index |
vmware:esxlog:<service-name> |
vmware:esxlog:<service-name> |
infraops |
The service-name in the source and sourcetype is the same as the service label, for example, vmware:esxlog:vmware
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: VMWARE_ESX.
Earlier name/vendor
4.3 - NSX
NSX:
Provides network virtualization, micro-segmentation, and security for software-defined data centers.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Configure your NSX appliances, NSX Edges, and hypervisors to send their logs to the Syslog (autodetect and classify) connector of an AxoRouter instance. Use either:
- The TCP protocol (port 601 when using the default connector), or
- TLS-encrypted TCP protocol (port 6514 when using the default connector)
For details on configuring NSX, see Configure Remote Logging in the NSX Administration Guide.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
vmware:nsxlog:dfwpktlogs |
netfw |
vmware:nsxlog:firewall-pktlog |
netfw |
vmware:nsxlog:nsx |
infraops |
vmware:nsxlog:nsxv |
infraops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: VMWARE_NSX.
Earlier name/vendor
- VMware NSX
- NSX-T Data Center
4.4 - vCenter
vCenter:
vCenter is a centralized management platform that provides a single console for managing an entire VMware vSphere virtual infrastructure, including multiple ESXi hosts and virtual machines.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label |
Message field |
value |
vendor |
meta.vendor |
broadcom |
product |
meta.product |
vcenter |
service |
meta.service.name |
vpxd, vws, stats, cim-diag, sms, vim, cis-license, applmgmt-audit, updatemgr, vmafdd, vmcad, vmdird, vmon, osfsd, wcpxsvc, wcpsvc, mbcs, vmcam, vpostgres, vsphere, vcha, vcenter-server |
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| source |
sourcetype |
index |
vmware:vclog:<service-name> |
vmware:vclog:<service-name> |
infraops |
The service-name in the source and sourcetype is the same as the service label, for example, vmware:vclog:vmon
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: VMWARE_VCENTER.
Earlier name/vendor
5 - Check Point
5.1 - Anti-Bot
Anti-Bot:
Detects and blocks botnet communications and command-and-control traffic to prevent malware infections.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:endpoint |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_EDR.
5.2 - Anti-Malware
Anti-Malware:
Protects endpoints from viruses, ransomware, and other malware using signature and behavior analysis.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:endpoint |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_EDR.
5.3 - Anti-Phishing
Anti-Phishing:
Prevents phishing attacks by analyzing email content and links to block credential theft attempts.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:email |
email |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_EMAIL.
5.4 - Anti-Spam and Email Security
Anti-Spam and Email Security:
Blocks spam and malicious email content using reputation checks and email filtering techniques.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:email |
email |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_EMAIL.
5.5 - CPMI Client
CPMI Client:
Legacy Check Point management client used to interface with security policies and logs.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cp_log |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_FIREWALL.
5.6 - cpmidu_update_tool
cpmidu_update_tool:
Utility used to update configuration and database files for Check Point Multi-Domain environments.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:audit |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_FIREWALL.
5.7 - Database Tool
Database Tool:
Command-line tool to extract, query, or update Check Point configuration and policy databases.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:audit |
netops |
5.8 - Edge Secure Web Gateway (Edge SWG)
Edge Secure Web Gateway (Edge SWG):
Provides configuration profiles for secure mobile access and web filtering on iOS devices.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:network |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_HARMONY.
5.9 - Endpoint Compliance
Endpoint Compliance:
Checks endpoint status and posture before granting network access, enforcing security policies.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:endpoint |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_EDR.
5.10 - Endpoint Management
Endpoint Management:
Centralized platform for managing endpoint protection, updates, and policy enforcement.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:endpoint |
netops |
5.11 - Forensics
Forensics:
Analyzes security incidents on endpoints to uncover attack vectors and malicious activity.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:endpoint |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_EDR.
5.12 - GO Password Reset
GO Password Reset:
Facilitates secure password reset processes for users across integrated environments.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:audit |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_AUDIT.
5.13 - HTTPS Inspection
HTTPS Inspection:
Decrypts and inspects HTTPS traffic to detect hidden threats within encrypted web sessions.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:firewall |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_FIREWALL.
5.14 - IPS
IPS:
Detects and blocks known and unknown exploits, malware, and vulnerabilities in network traffic.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:ids |
netids |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_EDR.
5.15 - MDS Query Tool
MDS Query Tool:
CLI tool for querying multi-domain configurations and policies in Check Point environments.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cp_log |
netops |
5.16 - Media Encryption & Port Protection
Media Encryption & Port Protection:
Secures USB ports and encrypts removable media to protect sensitive data on endpoints.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:endpoint |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_EDR.
5.17 - Mobile Access
Mobile Access:
Enables secure remote access to corporate apps and data from mobile devices.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:network |
netops |
5.18 - Next-Generation Firewall (NGFW)
Next-Generation Firewall (NGFW):
Next-generation firewall providing intrusion prevention, application control, and threat protection.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:firewall |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_FIREWALL.
5.19 - QoS
QoS:
Implements bandwidth control and traffic prioritization policies for optimized network usage.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:firewall |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_FIREWALL.
5.20 - Quantum
Quantum:
Unified threat prevention platform delivering firewall, VPN, and intrusion prevention capabilities.
If you’d like to send data from this source to AxoRouter, contact our support team for details.
5.21 - Query Database
Query Database:
Accesses and queries internal policy or object databases in Check Point systems.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:audit |
netops |
5.22 - SmartConsole
SmartConsole:
Graphical interface for managing Check Point security policies, logs, and monitoring.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:audit |
netops |
5.23 - SmartUpdate
SmartUpdate:
Tool for updating and managing licenses, software, and hotfixes in Check Point environments.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:audit |
netops |
5.24 - Threat Emulation and Anti-Exploit
Threat Emulation and Anti-Exploit:
Emulates files in a virtual environment to detect and block advanced persistent threats and exploits.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:endpoint |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_EDR.
5.25 - URL Filtering
URL Filtering:
Controls and logs web access based on URL categories and custom site rules to enforce policy.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:firewall |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CHECKPOINT_FIREWALL.
5.26 - Web API
Web API:
Provides programmatic access to Check Point security management through RESTful API endpoints.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cp_log |
checkpoint:audit |
netops |
6 - Cisco
6.1 - Access Control System (ACS)
Access Control System (ACS):
Centralizes network access control with RADIUS and TACACS+ for authentication and authorization.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:acs |
netauth |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_ACS.
6.2 - Adaptive Security Appliance (ASA)
Adaptive Security Appliance (ASA):
Provides stateful firewall, VPN support, and advanced threat protection for secure network perimeters.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:asa |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_ASA_FIREWALL.
6.3 - Application Control Engine (ACE)
Application Control Engine (ACE):
Provides application-aware load balancing, SSL offload, and traffic control for Cisco networks.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:ace |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_ACE.
6.4 - Cisco IOS
Cisco IOS:
Network operating system for Cisco routers and switches, enabling routing, switching, and security.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:ios |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_IOS.
6.5 - Digital Network Architecture (DNA)
Digital Network Architecture (DNA):
Provides software-defined networking, policy automation, and analytics for enterprise infrastructure.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:dna |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_DNAC.
6.6 - Email Security Appliance (ESA)
Email Security Appliance (ESA):
Protects email systems from spam, phishing, malware, and data loss with advanced threat filtering.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Note that the device can be configured to send plain-text syslog or CEF-formatted logs. AxoRouter can automatically parse all flavors.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, index, and source settings:
| sourcetype |
index |
source |
| cisco:esa:http |
email |
esa:http |
| cisco:esa:textmail |
email |
esa:textmail |
| cisco:esa:amp |
email |
esa:amp |
| cisco:esa:antispam |
email |
esa:antispam |
| cisco:esa:system_logs |
email |
esa:system_logs |
| cisco:esa:system_logs |
email |
esa:euq_logs |
| cisco:esa:system_logs |
email |
esa:service_logs |
| cisco:esa:system_logs |
email |
esa:reportd_logs |
| cisco:esa:system_logs |
email |
esa:sntpd_logs |
| cisco:esa:system_logs |
email |
esa:smartlicense |
| cisco:esa:error_logs |
email |
esa:error_logs |
| cisco:esa:error_logs |
email |
esa:updater_logs |
| cisco:esa:content_scanner |
email |
esa:content_scanner |
| cisco:esa:authentication |
email |
esa:authentication |
| cisco:esa:http |
email |
esa:http |
| cisco:esa:textmail |
email |
esa:textmail |
| cisco:esa:amp |
email |
esa:amp |
| cisco:esa |
email |
program: <variable> |
| cisco:esa:cef |
email |
esa:consolidated |
Tested with: Splunk Add-on for Cisco ESA
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_EMAIL_SECURITY.
6.7 - Firepower
Firepower:
Provides next-gen firewall features including intrusion prevention, app control, and malware protection.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:firepower:syslog |
netids |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_FIREPOWER_FIREWALL.
6.8 - Firepower Threat Defence (FTD)
Firepower Threat Defence (FTD):
Unifies firewall, VPN, and intrusion prevention into a single software for comprehensive threat defense.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:ftd |
netfw |
6.9 - Firewall Services Module (FWSM)
Firewall Services Module (FWSM):
Delivers multi-context, high-performance firewall services integrated into Cisco Catalyst switches.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:fwsm |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_FWSM.
6.10 - HyperFlex (HX, UCSH)
HyperFlex (HX, UCSH):
Infrastructure solution combining compute, storage, and networking in a single system.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:ucsh:hx |
infraops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_UCS.
6.11 - Identity Services Engine (ISE)
Identity Services Engine (ISE):
Manages network access control and enforces policies with user and device authentication capabilities.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
For details on configuring your Identity Services Engine to forward its logs to an AxoRouter instance, see Configure Remote Syslog Collection Locations in Cisco Identity Services Engine (ISE) Administrator Guide.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:ise:syslog |
netauth |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_ISE.
6.12 - Integrated Management Controller (IMC)
Integrated Management Controller (IMC):
Provides out-of-band server management for Cisco UCS, enabling hardware monitoring and configuration.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:cimc |
infraops |
6.13 - IOS XR
IOS XR:
High-performance, modular network operating system for carrier-grade routing and scalability.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:xr |
netops |
6.14 - Meraki MX
Meraki MX:
Cloud-managed network appliance offering firewall, VPN, SD-WAN, and security in a single platform.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:meraki |
netfw |
Tested with: TA-meraki
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_MERAKI.
6.15 - Private Internet eXchange (PIX)
Private Internet eXchange (PIX):
Legacy firewall appliance delivering stateful inspection and secure network access control.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:pix |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_PIX_FIREWALL.
6.16 - TelePresence Video Communication Server (VCS)
TelePresence Video Communication Server (VCS):
Enables video conferencing control and call routing for Cisco TelePresence systems and endpoints.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:tvcs |
main |
6.17 - Unified Computing System Manager (UCSM)
Unified Computing System Manager (UCSM):
Centralized management platform for Cisco Unified Computing System (UCS) servers and resources.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:ucs |
infraops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_UCS.
6.18 - Unified Communications Manager (UCM)
Unified Communications Manager (UCM):
Delivers unified voice, video, messaging, and mobility services in enterprise IP telephony systems.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:ucm |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_UCM.
6.19 - Viptela
Viptela:
Software-defined WAN solution providing secure connectivity, centralized control, and traffic optimization.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cisco:viptela |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CISCO_VIPTELA.
7 - Citrix
7.1 - Netscaler
Netscaler:
Offers application delivery, load balancing, and security features for optimized app performance.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
citrix:netscaler:appfw:cef |
netfw |
citrix:netscaler:syslog |
netfw |
citrix:netscaler:appfw |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CITRIX_NETSCALER_WEB_LOGS.
8 - Corelight
8.1 - Open Network Detection & Response (NDR)
Open Network Detection & Response (NDR):
Provides network detection and response by analyzing traffic for advanced threats and anomalous behavior.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
index |
corelight_alerts |
main |
corelight_conn |
main |
corelight_corelight |
main |
corelight_corelight_metrics_bro |
main |
corelight_corelight_metrics_iface |
main |
corelight_dhcp |
main |
corelight_dpd |
main |
corelight_etc_viz |
main |
corelight_evt_all |
main |
corelight_evt_http |
main |
corelight_evt_suri |
main |
corelight_files |
main |
corelight_ftp |
main |
corelight_http |
main |
corelight_http_red |
main |
corelight_idx |
main |
corelight_irc |
main |
corelight_kerberos |
main |
corelight_metrics_bro |
main |
corelight_metrics_iface |
main |
corelight_rdp |
main |
corelight_smb |
main |
corelight_smb_files |
main |
corelight_socks |
main |
corelight_ssh |
main |
corelight_ssh_red |
main |
corelight_ssl |
main |
corelight_st_base |
main |
corelight_suri |
main |
corelight_suricata_corelight |
main |
corelight_x509 |
main |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CORELIGHT.
9 - CyberArk
9.1 - Privileged Threat Analytics (PTA)
Privileged Threat Analytics (PTA):
Analyzes privileged account behavior to detect threats and suspicious activity in real time.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cyberark:pta:cef |
main |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CYBERARK_PTA.
9.2 - Vault
Vault:
Stores and manages privileged credentials, session recordings, and access control policies securely.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
cyberark:epv:cef |
netauth |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: CYBERARK.
10 - F5 Networks
10.1 - BIG-IP
BIG-IP:
Provides load balancing, traffic management, and application security for optimized service delivery.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Note that the device can be configured to send logs formatted as plain-text syslog, JSON, or key-value pairs. AxoRouter can automatically parse all flavors.
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label |
Message field |
value |
vendor |
meta.vendor |
f5 |
product |
meta.product |
bigip |
service |
meta.service.name |
ASM, apmd, audit_forwarder, CROND, F5, httpd, mcpd, sshd, sshd(pam_audit), systemd-journal, tmm, tmm1, tmm2, tmsh |
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
| f5:bigip:syslog |
netops |
| f5:bigip:ltm:access_json |
netops |
| f5:bigip:asm:syslog |
netops |
| f5:bigip:apm:syslog |
netops |
| f5:bigip:ltm:ssl:error |
netops |
| f5:bigip:ltm:tcl:error |
netops |
| f5:bigip:ltm:traffic |
netops |
| f5:bigip:ltm:log:error |
netops |
| f5:bigip:gtm:dns:request:irule |
netops |
| f5:bigip:gtm:dns:response:irule |
netops |
| f5:bigip:ltm:http:irule |
netops |
| f5:bigip:ltm:failed:irule |
netops |
| nix:syslog |
netops |
Tested with: Splunk Add-on for F5 BIG-IP
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: F5_BIGIP_APM.
11 - FireEye
12 - Forcepoint
12.1 - Email Security
Email Security:
Protects email systems from spam, phishing, malware, and data exfiltration using advanced threat defense.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
index |
forcepoint:email:cef |
email |
forcepoint:email:kv |
email |
forcepoint:email:leef |
email |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORCEPOINT_EMAILSECURITY.
Earlier name/vendor
12.2 - Next-Generation Firewall (NGFW)
Next-Generation Firewall (NGFW):
Next-gen firewall with deep packet inspection, policy enforcement, and integrated intrusion prevention.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
index |
websense:cg:cef |
netproxy |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORCEPOINT_FIREWALL.
Earlier name/vendor
12.3 - WebProtect
WebProtect:
Provides web traffic filtering, malware protection, and data loss prevention for secure internet access.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
index |
websense:cg:cef |
netproxy |
websense:cg:kv |
netproxy |
websense:cg:leef |
netproxy |
Earlier name/vendor
13 - Fortinet
13.1 - FortiGate firewalls
FortiGate firewalls:
Enterprise firewall platform offering threat protection, VPN, and traffic filtering for secure networking.
The following sections show you how to configure FortiGate Next-Generation Firewall (NGFW) to send their log data to Axoflow.
CAUTION:
Make sure to set data forwarding on your appliances/servers as described in this guide. Different settings like alternate message formats or ports might be valid, but can result in data loss or incorrect parsing.
Prerequisites
Steps
Note: The steps involving the FortiGate user interface are just for your convenience, for details, see the official FortiGate documentation.
-
Log in to your FortiGate device. You need administrator privileges to perform the configuration.
-
Register the address of your AxoRouter as an Address Object.
-
Select Log & Report > Log Settings > Global Settings.
-
Configure the following settings:
- Event Logging: Click All.
- Local traffic logging: Click All.
- Syslog logging: Enable this option.
- IP address/FQDN: Enter the address of your AxoRouter:
%axorouter-ip%
-
Click Apply.
-
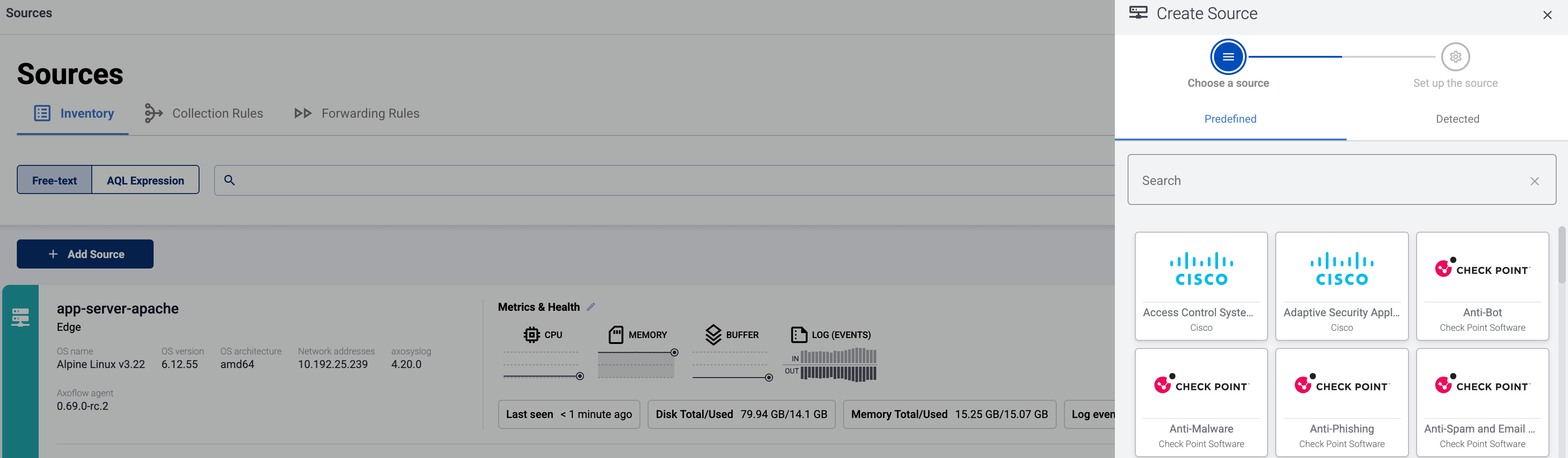
Add the source to AxoConsole.
-
Open the AxoConsole and select Topology.
-
Select Add Item > Source.
-
If the source is actively sending data to an AxoRouter instance, select Detected, then select your source.
-
Otherwise, select the vendor and product corresponding to your source from the Predefined sources, then enter the parameters of the source, like IP address and FQDN.
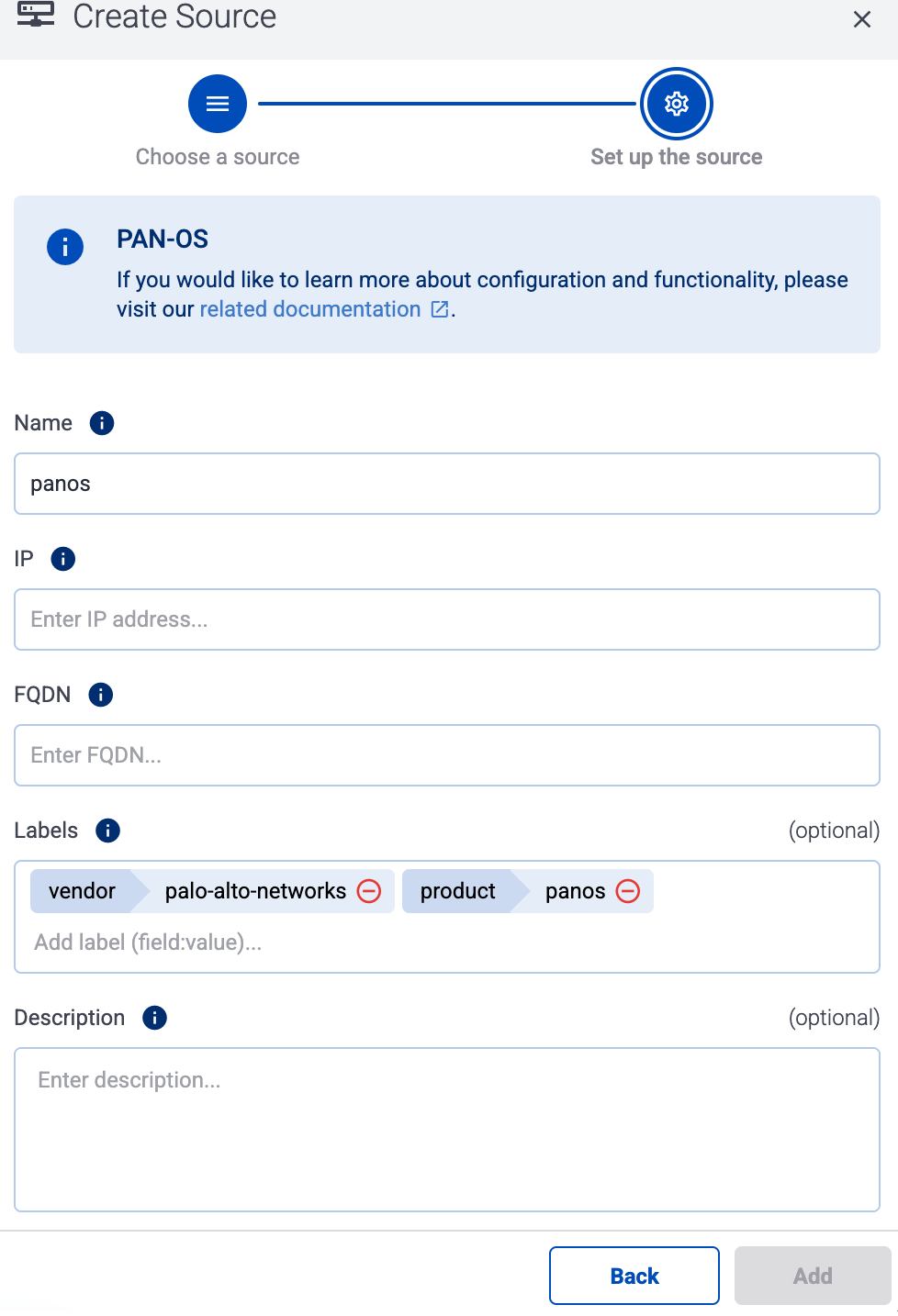
Note
During
log tapping, you can add hosts that are actively sending data to an AxoRouter instance by clicking
Register source.
-
(Optional) Add custom labels as needed.
-
Select Add.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
fortigate_event |
netops |
fortigate_traffic |
netfw |
fortigate_utm |
netfw |
Tested with: Fortinet FortiGate Add-On for Splunk technical add-on
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORTINET_FIREWALL.
13.2 - FortiMail
FortiMail:
Secures inbound and outbound email with spam filtering, malware protection, and advanced threat detection.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
fml:log |
email |
Tested with: FortiMail Add-on for Splunk technical add-on
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORTINET_FORTIMAIL.
13.3 - FortiProxy
FortiProxy:
Protects from internet threats like malware, phishing, and data loss by inspecting web traffic, filtering content, controlling applications, and enforcing security policies
To send logs from FortiProxy to AxoRouter, configure remote logging to a syslog server on FortiProxy. Use the IP address of AxoRouter as the syslog server IP address. Set FortiProxy to send logs in the default format. (If you need to send the logs in CEF format, contact our support team). For details, see Generic tips.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
fortiproxy_anomaly |
netfw |
fortiproxy_event |
netops |
fortiproxy_traffic |
netfw |
fortiproxy_utm |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORTINET_WEBPROXY.
13.4 - FortiWeb
FortiWeb:
Web application firewall protecting websites from attacks like XSS, SQL injection, and bot threats.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
fwb_log |
netops |
fwb_attack |
netids |
fwb_event |
netops |
fwb_traffic |
netfw |
Tested with: Fortinet FortiWeb Add-0n for Splunk technical add-on
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORTINET_FORTIWEB.
14 - Fortra
14.1 - Powertech SIEM Agent for IBM i
Powertech SIEM Agent for IBM i:
Monitors IBM i system activity and forwards security events for centralized analysis in SIEM platforms.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Note that the device can be configured to send logs formatted as CEF or LEEF. AxoRouter can automatically parse all flavors.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
source |
index |
PowerTech:SIEMAgent:cef |
PowerTech:SIEMAgent |
netops |
PowerTech:SIEMAgent:leef |
PowerTech:SIEMAgent |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORTRA_POWERTECH_SIEM_AGENT.
Earlier name/vendor
Powertech Interact
15 - General Unix/Linux host
15.1 - Generic Linux services
Generic Linux services:
A generic placeholder for program classifications
These classifications include non-vendor specific services and applications commonly found on Linux/Unix hosts.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label |
Message field |
value |
vendor |
meta.vendor |
nix |
product |
meta.product |
generic |
service |
meta.service.name |
bind, chronyd, cron, cupsd, dbus-daemon, dhcpd, dnsmasq, dnf, dockerd, NetworkManager, nginx, nxlog, rsyslogd, sshd, su, sudo, syslog-ng, or systemd |
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| source |
sourcetype |
index |
program:chron |
nix:syslog |
netops |
program:chronyd |
nix:syslog |
netops |
program:cupsd |
nix:syslog |
netops |
program:dbus-daemon |
nix:syslog |
netops |
program:dhcpd |
isc:dhcpd |
netipam |
program:dnf |
nix:syslog |
netops |
program:dockerd |
nix:syslog |
netops |
program:dnsmasq |
nix:syslog |
netdns |
program:named |
isc:bind:network |
netdns |
program:NetworkManager |
nix:syslog |
netops |
program:nxlog |
nix:syslog |
netops |
program:rsyslogd |
nix:syslog |
netops |
program:sshd |
nix:syslog |
netops |
program:su |
nix:syslog |
netauth |
program:sudo |
nix:syslog |
netauth |
program:syslog-ng |
nix:syslog |
netops |
program:systemd |
nix:syslog |
netops |
Tested with: Splunk Add-on for Infoblox
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: BIND_DNS, ISC_DHCP, NIX_SYSTEM, or OPENSSH.
16 - Imperva
16.1 - Incapsula
Incapsula:
Cloud-based WAF, DDoS protection, and bot mitigation service for securing web applications and APIs.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
source |
index |
cef |
Imperva:Incapsula |
netwaf |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: IMPERVA_CEF.
16.2 - SecureSphere
SecureSphere:
Provides on-prem web application, database, and file security with granular activity monitoring.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
index |
imperva:waf:firewall:cef |
netwaf |
imperva:waf:security:cef |
netwaf |
imperva:waf |
netwaf |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: IMPERVA_SECURESPHERE.
17 - Infoblox
17.1 - NIOS
NIOS:
Delivers secure DNS, DHCP, and IPAM (DDI) services with centralized network control and automation.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
source |
infoblox:threatprotect |
netids |
Infoblox:NIOS |
infoblox:dns |
netids |
Infoblox:NIOS |
Tested with: Splunk Add-on for Infoblox
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: INFOBLOX, INFOBLOX_DNS.
18 - Ivanti
18.1 - Connect secure
Connect secure:
Provides dynamic IP address assignment and network configuration for DHCP-enabled devices.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
source |
index |
pulse:connectsecure |
|
netfw |
pulse:connectsecure:web |
|
netproxy |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: IVANTI_CONNECT_SECURE.
Earlier name/vendor
Pulse Connect Secure
19 - Juniper
19.1 - Junos OS
Junos OS:
Junos OS is the network operating system for Juniper physical and virtual networking and security products.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label |
Message field |
value |
vendor |
meta.vendor |
juniper |
product |
meta.product |
junos |
service |
meta.service.name |
eswd, ifinfo, mcsnoopd, mgd, mib2d, rpd, RT_AAMW, RT_FLOW, RT_IDP, RT_SECINTEL, RT_UTM, tfeb0 |
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
juniper:junos:aamw:structured |
netfw |
juniper:junos:firewall |
netfw |
juniper:junos:firewall |
netids |
juniper:junos:firewall:structured |
netfw |
juniper:junos:firewall:structured |
netids |
juniper:junos:idp |
netids |
juniper:junos:idp:structured |
netids |
juniper:legacy |
netops |
juniper:junos:secintel:structured |
netfw |
juniper:junos:snmp |
netops |
juniper:structured |
netops |
Tested with: Splunk Add-on for Juniper
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: JUNIPER_JUNOS.
20 - Kaspersky
20.1 - Endpoint Security
Endpoint Security:
Protects endpoints from malware, ransomware, and intrusions with antivirus, firewall, and threat detection.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Note that the device can be configured to send logs formatted as plain-text syslog, CEF, or LEEF. AxoRouter can automatically parse all flavors.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Note that the device can be configured to send plain syslog text, LEEF, or CEF-formatted output.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
kaspersky:cef |
epav |
kaspersky:es |
epav |
kaspersky:gnrl |
epav |
kaspersky:klau |
epav |
kaspersky:klbl |
epav |
kaspersky:klmo |
epav |
kaspersky:klna |
epav |
kaspersky:klpr |
epav |
kaspersky:klsr |
epav |
kaspersky:leef |
epav |
kaspersky:sysl |
epav |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: KASPERSKY_ENDPOINT.
21 - Kubernetes
21.1 - NGINX Ingress
NGINX Ingress:
Ingress NGINX Controller
Configure your log collector (for example, Telemetry Controller) to send data to an OpenTelemetry Connector of an AxoRouter instance using the OTLP/gRPC protocol.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
21.2 - Telemetry Controller
Telemetry Controller:
Telemetry Controller
Configure Telemetry Controller to send data to an OpenTelemetry Connector of an AxoRouter instance.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
22 - MicroFocus
23 - Microsoft
23.1 - Azure Event Hubs
Azure Event Hubs:
Big data streaming platform to ingest and process events.
Axoflow can collect data from your Azure Event Hubs. At a high level, the process looks like this:
- Deploy an Axoflow Cloud Connector that will collect the data from your Event Hub. Axoflow Cloud Connector is a simple container that you can deploy into Azure, another cloud provider, or on-prem.
- The connector forwards the collected data to the OpenTelemetry connector of an AxoRouter instance. This AxoRouter can be deployed within Azure, another cloud provider, or on-prem.
- Configure a Flow on AxoConsole that processes and routes the collected data to your destination (for example, Splunk or another SIEM).

Prerequisites
Steps
To collect data from Azure Event Hubs, complete the following steps.
-
Deploy an Axoflow Cloud Connector into Azure.
-
Access the Kubernetes node or virtual machine.
-
Set the following environment variable to the IP address of the AxoRouter where you want to forward the data from Event Hubs. This IP address must be accessible from the connector. You can find the IP address of AxoRouter on the Routers > AxoRouter > Overview page.
export AXOROUTER_ENDPOINT=<AxoRouter-IP-address>
-
(Optional) By default, the connector stores positional and other persistence-related data in the /etc/axoflow-otel-collector/storage directory. In case you want to use a different directory, set the STORAGE_DIRECTORY environment variable.
-
Run the following command to generate a UUID for the connector. AxoConsole will use this ID to identify the connector.
UUID_FULL=$(uuidgen 2>/dev/null || cat /proc/sys/kernel/random/uuid 2>/dev/null || python3 -c "import uuid; print(uuid.uuid4())")
export AXOCLOUDCONNECTOR_DEVICE_ID=$(echo "$UUID_FULL" | cut -d'-' -f1)
-
Set TLS encryption to secure the communication between Axoflow Cloud Connector and AxoRouter.
Configure the TLS-related settings of Axoflow Cloud Connector using the following environment variables.
| Variable |
Required |
Default |
Description |
AXOROUTER_TLS_INSECURE |
No |
false |
Disables TLS encryption if set to true |
AXOROUTER_TLS_INCLUDE_SYSTEM_CA_CERTS_POOL |
No |
false |
Set to true to use the system CA certificates |
AXOROUTER_TLS_CA_FILE |
No |
- |
Path to the CA certificate file used to validate the certificate of AxoRouter |
AXOROUTER_TLS_CA_PEM |
No |
- |
PEM-encoded CA certificate |
AXOROUTER_TLS_INSECURE_SKIP_VERIFY |
No |
false |
Set to true to disable TLS certificate verification of AxoRouter |
AXOROUTER_TLS_CERT_FILE |
No |
- |
Path to the certificate file of Axoflow Cloud Connector |
AXOROUTER_TLS_CERT_PEM |
No |
- |
PEM-encoded client certificate |
AXOROUTER_TLS_KEY_FILE |
No |
- |
Path to the client private key file of Axoflow Cloud Connector |
AXOROUTER_TLS_KEY_PEM |
No |
- |
PEM-encoded client private key |
AXOROUTER_TLS_MIN_VERSION |
No |
1.2 |
Minimum TLS version to use |
AXOROUTER_TLS_MAX_VERSION |
No |
- |
Maximum TLS version to use |
Note
You’ll have to include the TLS-related environment variables you set in the docker command used to deploy Axoflow Cloud Connector.
-
Set the AZURE_EVENTHUB_CONNECTION_STRING environment variable.
export AZURE_EVENTHUB_CONNECTION_STRING="Endpoint=sb://<NamespaceName>.servicebus.windows.net/;SharedAccessKeyName=<KeyName>;SharedAccessKey=<KeyValue>;EntityPath=<EventHubName>"
-
Deploy the Axoflow Cloud Connector by running the following command. Also, pass the TLS-related settings you’ve set earlier.
docker run --rm \
-v "${STORAGE_DIRECTORY}":"${STORAGE_DIRECTORY}" \
-e AZURE_EVENTHUB_CONNECTION_STRING="${AZURE_EVENTHUB_CONNECTION_STRING}" \
-e AXOROUTER_ENDPOINT="${AXOROUTER_ENDPOINT}" \
-e STORAGE_DIRECTORY="${STORAGE_DIRECTORY}" \
-e <TlS-related-environment-variable>="${<TlS-related-environment-variable>}" \
-e AXOCLOUDCONNECTOR_DEVICE_ID="${AXOCLOUDCONNECTOR_DEVICE_ID}" \
ghcr.io/axoflow/axocloudconnectors:latest
The Axoflow Cloud Connector starts forwarding logs to the AxoRouter instance.
-
Add the appliance to AxoConsole.
- Open the AxoConsole and select Topology.
- Select Add Item > Source.
- Select Azure Event Hubs.
- Enter the IP address and the FQDN of the Axoflow Cloud Connector instance.
- Select Add.
-
Create a Flow to route the data from the AxoRouter instance to a destination. You can use the Labels of this source to select messages from this source.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Event Hubs Audit logs labels
Event Hubs Provisioning logs labels
| Analytics label |
Message field |
value |
vendor |
meta.vendor |
microsoft |
product |
meta.product |
azure-event-hubs-provisioning |
Event Hubs Signin logs labels
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
mscs:azure:eventhub:log |
azure-activity |
Configure the TLS-related settings of Axoflow Cloud Connector using the following environment variables.
| Variable |
Required |
Default |
Description |
AXOROUTER_TLS_INSECURE |
No |
false |
Disables TLS encryption if set to true |
AXOROUTER_TLS_INCLUDE_SYSTEM_CA_CERTS_POOL |
No |
false |
Set to true to use the system CA certificates |
AXOROUTER_TLS_CA_FILE |
No |
- |
Path to the CA certificate file used to validate the certificate of AxoRouter |
AXOROUTER_TLS_CA_PEM |
No |
- |
PEM-encoded CA certificate |
AXOROUTER_TLS_INSECURE_SKIP_VERIFY |
No |
false |
Set to true to disable TLS certificate verification of AxoRouter |
AXOROUTER_TLS_CERT_FILE |
No |
- |
Path to the certificate file of Axoflow Cloud Connector |
AXOROUTER_TLS_CERT_PEM |
No |
- |
PEM-encoded client certificate |
AXOROUTER_TLS_KEY_FILE |
No |
- |
Path to the client private key file of Axoflow Cloud Connector |
AXOROUTER_TLS_KEY_PEM |
No |
- |
PEM-encoded client private key |
AXOROUTER_TLS_MIN_VERSION |
No |
1.2 |
Minimum TLS version to use |
AXOROUTER_TLS_MAX_VERSION |
No |
- |
Maximum TLS version to use |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: AZURE_EVENTHUB.
23.2 - Cloud App Security (MCAS)
Cloud App Security (MCAS):
Monitors cloud app usage, detects anomalies, and enforces security policies across SaaS services.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
cef |
microsoft:cas |
main |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: MICROSOFT_DEFENDER_CLOUD_ALERTS.
23.3 - Windows hosts
Windows hosts:
Event logs from core services like security, system, DNS, and DHCP for operational and forensic analysis.
To collect event logs from Microsoft Windows hosts, Axoflow supports both agent-based and agentless methods.
Labels
Labels assigned to data received from Windows hosts depend on how AxoRouter receives the data. For details, see Windows host - agent based solution and Windows Event Collector (WEC).
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
windows:eventlog:snare |
oswin |
windows:eventlog:xml |
oswin |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: WINEVTLOG, WINEVTLOG_XML, WINDOWS_DHCP, WINDOWS_DNS.
24 - MikroTik
24.1 - RouterOS
RouterOS:
Router operating system providing firewall, bandwidth management, routing, and hotspot functionality.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
routeros |
netfw |
routeros |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: MIKROTIK_ROUTER.
25 - NetFlow Logic
25.1 - NetFlow Optimizer
NetFlow Optimizer:
Aggregates and transforms flow data (NetFlow, IPFIX) into actionable security and performance insights.
The following sections show you how to configure NetFlow Optimizer to send their log data to Axoflow.
CAUTION:
Make sure to set data forwarding on your appliances/servers as described in this guide. Different settings like alternate message formats or ports might be valid, but can result in data loss or incorrect parsing.
Prerequisites
Steps
Note: The steps involving the NetFlow Optimizer user interface are just for your convenience, for details, see the official documentation.
-
Log in to NetFlow Optimizer.
-
Select Outputs, then click the plus sign to add an output to NetFlow Optimizer.
-
Configure a Syslog (UDP) output:
- Name: Enter a name for the output, for example,
Axoflow.
- Address: The IP address of the AxoRouter instance where you want to send the messages.
- Port: Set this parameter to 514.
-
Click Save.
-
Add the source to AxoConsole.
-
Open the AxoConsole and select Topology.
-
Select Add Item > Source.

-
If the source is actively sending data to an AxoRouter instance, select Detected, then select your source.
-
Otherwise, select the vendor and product corresponding to your source from the Predefined sources, then enter the parameters of the source, like IP address and FQDN.

Note
During
log tapping, you can add hosts that are actively sending data to an AxoRouter instance by clicking
Register source.
-
(Optional) Add custom labels as needed.
-
Select Add.
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label |
Message field |
value |
vendor |
meta.vendor |
netflow |
product |
meta.product |
optimizer |
service |
meta.service.name |
Network Conversations Monitor, SNMP Custom OID Sets Monitor, Sampling Monitor, SNMP Information Monitor, DNS Service Monitor, DNS Users Monitor, Network Subnets Monitor, Asset Access Monitor, Services Performance Monitor, Top Bandwidth Consumers for Cisco ASA, Top Traffic Destinations for Cisco ASA, Top Policy Violators for Cisco ASA, Top Hosts with most Connections for Cisco ASA, Outbound Mail Spammers Monitor, Inbound Mail Spammers Monitor, Unauthorized Mail Servers Monitor, Rejected Emails Monitor, Top Bandwidth Consumers for Palo Alto Networks Firewall, Top Traffic Destinations for Palo Alto Networks Firewall, Hosts with Most Policy Violations for Palo Alto Networks Firewall, Most Active Hosts for Palo Alto Networks Firewall, Bandwidth Consumption per Application for Palo Alto Networks Firewall, Bandwidth Consumption per Application/User for Palo Alto Networks, Top Applications Traffic Monitor, Top Applications Host Pairs Monitor, Visitors by Country, Botnet C&C Traffic Monitor, Custom Threat lists Monitor, Host Reputation Monitor, Threat Feeds Traffic Monitor, TCP Health Monitor, Network Conversations Monitor, Top Connections Monitor, Top Pairs Monitor, CBQoS Monitor, Traffic by Autonomous Systems, Top Traffic Monitor, Top Packets Monitor, SNMP Custom OID Sets Monitor, Top Bandwidth Consumers for NSX Distributed Firewall, Top Traffic Destinations for NSX Distributed Firewall, Top Policy Violators for NSX Distributed Firewall, Top Hosts with most Connections for NSX Distributed Firewall, Top Host VM:Host Pairs, Top VM:Host Traffic Monitor, AWS VPC Flow logs, Micro-segmentation Top Pairs Monitor, AWS Top Traffic Monitor, GCP VPC Flow Logs, GCP Top Traffic Monitor, Azure NSG Flow Logs, Cisco AVC Top Applications Monitor, Cisco AVC Bandwidth Consumption Monitor, Azure Top Traffic Monitor, Cisco AnyConnect Top Traffic Monitor, SNMP Traps Monitor, Auto-discovery Reporter, Top Traffic Monitor Geo City, Top Traffic Monitor Geo Country, Flow Data |
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
flowintegrator |
flowintegrator |
26 - Netgate
26.1 - pfSense
pfSense:
Open-source firewall and router platform with VPN, traffic shaping, and intrusion detection capabilities.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
pfsense:filterlog |
netfw |
pfsense:<program> |
netops |
The pfsense:<program> variant is simply a generic linux event that is generated by the underlying OS on the appliance.
Tested with: TA-pfsense
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: PFSENSE.
27 - Netmotion
27.1 - Netmotion
Netmotion:
Provides secure, optimized remote access with performance monitoring for mobile and distributed workforces.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
netmotion:reporting |
netops |
netmotion:mobilityserver:nm_mobilityanalyticsappdata |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: NETMOTION.
28 - NETSCOUT
28.1 - Arbor Edge Defense (AED)
Arbor Edge Defense (AED):
Edge-based DDoS protection and threat mitigation system to block attacks before they enter the network.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
source |
index |
netscout:aed |
netscout:aed |
netids |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: ARBOR_EDGE_DEFENSE.
28.2 - Arbor Pravail (APS)
Arbor Pravail (APS):
Monitors and mitigates advanced persistent threats and malware with inline packet inspection.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
source |
index |
netscout:aps |
netscout:aps |
netids |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: ARBOR_EDGE_DEFENSE.
Earlier name/vendor
- Arbor Networks Pravail (APS)
29 - Omnissa
Earlier name/vendor
VMware Horizon
29.1 - Horizon
Horizon:
Horizon is a platform for managing and delivering virtual desktops and applications to end-users across a variety of devices and locations.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
vmware:horizon |
infraops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: VMWARE_HORIZON.
Earlier name/vendor
VMware Horizon
30 - OpenText
30.1 - ArcSight
ArcSight:
SIEM platform for collecting, correlating, and analyzing security event data across IT environments.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
source |
index |
cef |
ArcSight:ArcSight |
main |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: ARCSIGHT_CEF.
Earlier name/vendor
MicroFocus ArcSight
30.2 - Self Service Password Reset (SSPR)
Self Service Password Reset (SSPR):
Allows users to securely reset their own passwords without IT assistance, reducing helpdesk load.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
index |
sspr |
netauth |
Earlier name/vendor
NetIQ Self Service Password Reset
31 - Palo Alto Networks
31.1 - Cortex XSOAR
Cortex XSOAR:
Security orchestration, automation, and response platform for threat detection and incident management.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype, source, and index settings:
| sourcetype |
source |
index |
cef |
tim:cef |
infraops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: PAN_XSOAR.
Earlier name/vendor
Threat Intelligence Management (TIM)
31.2 - Palo Alto firewalls
Palo Alto firewalls:
Firewall operating system delivering network security features including traffic control and threat prevention.
The following sections show you how to configure Palo Alto Networks Next-Generation Firewall devices to send their log data to Axoflow.
CAUTION:
Make sure to set data forwarding on your appliances/servers as described in this guide. Different settings like alternate message formats or ports might be valid, but can result in data loss or incorrect parsing.
Prerequisites
Steps
Note: The steps involving the Palo Alto Networks Next-Generation Firewall user interface are just for your convenience, for details, see the official PAN-OS® documentation.
-
Log in to your firewall device. You need administrator privileges to perform the configuration.
-
Configure a Syslog server profile.
-
Select Device > Server Profiles > Syslog.
-
Click Add and enter a Name for the profile, for example, axorouter.
-
Configure the following settings:
- Syslog Server: Enter the IP address of your AxoRouter:
%axorouter-ip%
- Transport: Select TCP or TLS.
- Port: Set the port to
601. (This is needed for the recommended IETF log format. If for some reason you need to use the BSD format, set the port to 514.)
- Format: Select IETF.
- Syslog logging: Enable this option.
-
Click OK.
-
Configure syslog forwarding for Traffic, Threat, and WildFire Submission logs. For details, see Configure Log Forwarding the official PAN-OS® documentation.
- Select Objects > Log Forwarding.
- Click Add.
- Enter a Name for the profile, for example,
axoflow.
- For each log type, severity level, or WildFire verdict, select the Syslog server profile.
- Click OK.
- Assign the log forwarding profile to a security policy to trigger log generation and forwarding.
- Select Policies > Security and select a policy rule.
- Select Actions, then select the Log Forwarding profile you created (for example,
axoflow).
- For Traffic logs, select one or both of the Log at Session Start and Log At Session End options.
- Click OK.
-
Configure syslog forwarding for System, Config, HIP Match, and Correlation logs.
- Select Device > Log Settings.
- For System and Correlation logs, select each Severity level, select the Syslog server profile, and click OK.
- For Config, HIP Match, and Correlation logs, edit the section, select the Syslog server profile, and click OK.
-
Click Commit.
-
Add the source to AxoConsole.
-
Open the AxoConsole and select Topology.
-
Select Add Item > Source.

-
If the source is actively sending data to an AxoRouter instance, select Detected, then select your source.
-
Otherwise, select the vendor and product corresponding to your source from the Predefined sources, then enter the parameters of the source, like IP address and FQDN.

Note
During
log tapping, you can add hosts that are actively sending data to an AxoRouter instance by clicking
Register source.
-
(Optional) Add custom labels as needed.
-
Select Add.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
pan:audit |
netops |
pan:globalprotect |
netfw |
pan:hipmatch |
epintel |
pan:traffic |
netfw |
pan:threat |
netproxy |
pan:system |
netops |
Tested with: Palo Alto Networks Add-on for Splunk technical add-on
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: PAN_FIREWALL.
32 - Ping Identity
32.1 - PingAccess
PingAccess:
A centralized access security solution which provides secure access to applications and APIs down to the URL level
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
source.engine |
pingaccess |
netauth |
Tested with: SecureAuth IdP Splunk App
33 - Powertech
34 - Progress
34.1 - Flowmon Anomaly Detection System (ADS)
Flowmon Anomaly Detection System (ADS):
Detects network anomalies and threats through flow-based behavior analysis and machine learning.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
flowmon-ads |
netids |
Earlier name/vendor
35 - Riverbed
35.1 - SteelConnect
SteelConnect:
WAN optimization appliance that accelerates application performance and reduces bandwidth usage.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label |
Message field |
value |
vendor |
meta.vendor |
riverbed |
product |
meta.product |
steelconnect |
service |
meta.service.name |
/opt/hal/bin/hal, alarmd, crld, domaind, hald_model, link_control, lumberjack_rbt-upgrader, lumberjack_rbt, mdreq, mgmtd, ocd, periodic_raidcheck, pm, rcud, restd, rgpd, rscored-upgrader, rscored, rstild-upgrader, rstild, sched, statsd, wdt, webasd |
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
riverbed:syslog |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: STEELHEAD.
35.2 - SteelHead
SteelHead:
Software-defined WAN solution for centralized network management and secure cloud connectivity.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
riverbed:steelhead |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: RIVERBED.
36 - RSA
36.1 - Authentication Manager
Authentication Manager:
Manages two-factor authentication using RSA SecurID tokens for secure access to enterprise resources.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
rsa:securid:admin:syslog |
netauth |
rsa:securid:system:syslog |
netauth |
rsa:securid:runtime:syslog |
netauth |
rsa:securid:syslog |
netauth |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: RSA_AUTH_MANAGER.
37 - rsyslog
Axoflow treats rsyslog sources as a generic syslog source. To send data from rsyslog to Axoflow, just configure rsyslog to send data to an AxoRouter instance using the syslog protocol.
Note that even if rsyslog is acting as a relay (receiving data from other clients and forwarding them to AxoRouter), on the Topology page it will be displayed as a data source.
Prerequisites
38 - SecureAuth
38.1 - Identity Platform
Identity Platform:
Delivers identity and access management with adaptive authentication and single sign-on capabilities.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
secureauth:idp |
netops |
Tested with: SecureAuth IdP Splunk App
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: SECUREAUTH_SSO.
39 - Skyhigh Security
39.1 - Secure Web Gateway
Secure Web Gateway:
Inspects and filters web traffic to protect against malware, enforce policies, and prevent data loss.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
mcafee:wg:leef |
mcafee:wg |
netproxy |
mcafee:wg:kv |
mcafee:wg |
netproxy |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: MCAFEE_WEBPROXY.
Earlier name/vendor
McAfee Secure Web Gateway
40 - SonicWall
40.1 - SonicWall
SonicWall:
Delivers firewall, VPN, and deep packet inspection to protect networks from cyber threats and intrusions.
The following sections show you how to configure SonicWall firewalls to send their log data to Axoflow.
CAUTION:
Make sure to set data forwarding on your appliances/servers as described in this guide. Different settings like alternate message formats or ports might be valid, but can result in data loss or incorrect parsing.
Prerequisites
Steps for SonicOS 7.x
Note: The steps involving the SonicWall user interface are just for your convenience, for details, see the official SonicWall documentation.
-
Log in to your SonicWall device. You need administrator privileges to perform the configuration.
-
Register the address of your AxoRouter as an Address Object.
-
Select MENU > OBJECT.
-
Select Match Objects > Addresses > Address objects.
-
Click Add Address.
-
Configure the following settings:
- Name: Enter a name for the AxoRouter, for example,
AxoRouter.
- Zone Assignment: Select the correct zone.
- Type: Select Host.
- IP Address: Enter the IP address of your AxoRouter:
%axorouter-ip%
-
Click Save.
-
Set your AxoRouter as a syslog server.
-
Navigate to Device > Log > Syslog.
-
Select the Syslog Servers tab.
-
Click Add.
-
Configure the following options:
- Name or IP Address: Select the Address Object of AxoRouter.
- Server Type: Select Syslog Server.
- Syslog Format: Select Enhanced.
If your Syslog server does not use default port 514, type the port number in the Port field.
By default, AxoRouter accepts data on the following ports (unless you’ve modified the default connector rules):
- 514 UDP and TCP for RFC3164 (BSD-syslog) and RFC5424 (IETF-syslog) formatted traffic. AxoRouter automatically recognizes and handles both formats.
- 601 TCP for RFC5424 (IETF-syslog) and RFC3164 (BSD-syslog) formatted traffic. AxoRouter automatically recognizes and handles both formats.
- 6514 TCP for TLS-encrypted syslog traffic.
- 4317 TCP for OpenTelemetry log data.
To receive data on other ports or other protocols, configure other connector rules for the AxoRouter host.
For TLS-encrypted syslog connections, create a new connector rule or edit an existing one, and configure the keys and certificates needed to encrypt the connections. For details, see Syslog.
Note
Make sure to enable the ports you’re using on the firewall of your host.
-
Add the source to AxoConsole.
-
Open the AxoConsole and select Topology.
-
Select Add Item > Source.

-
If the source is actively sending data to an AxoRouter instance, select Detected, then select your source.
-
Otherwise, select the vendor and product corresponding to your source from the Predefined sources, then enter the parameters of the source, like IP address and FQDN.

Note
During
log tapping, you can add hosts that are actively sending data to an AxoRouter instance by clicking
Register source.
-
(Optional) Add custom labels as needed.
-
Select Add.
Steps for SonicOS 6.x
Note: The steps involving the SonicWall user interface are just for your convenience, for details, see the official SonicWall documentation.
-
Log in to your SonicWall device. You need administrator privileges to perform the configuration.
-
Register the address of your AxoRouter as an Address Object.
-
Select MANAGE > Policies > Objects > Address Objects.
-
Click Add.
-
Configure the following settings:
- Name: Enter a name for the AxoRouter, for example,
AxoRouter.
- Zone Assignment: Select the correct zone.
- Type: Select Host.
- IP Address: Enter the IP address of your AxoRouter:
%axorouter-ip%
-
Click Add.
-
Set your AxoRouter as a syslog server.
-
Navigate to MANAGE > Log Settings > SYSLOG.
-
Click ADD.
-
Configure the following options:
- Syslog ID: Enter an ID for the firewall. This ID will be used as the hostname in the log messages.
- Name or IP Address: Select the Address Object of AxoRouter.
- Server Type: Select Syslog Server.
- Enable the Enhanced Syslog Fields Settings.
-
Click OK.
-
Add the source to AxoConsole.
-
Open the AxoConsole and select Topology.
-
Select Add Item > Source.

-
If the source is actively sending data to an AxoRouter instance, select Detected, then select your source.
-
Otherwise, select the vendor and product corresponding to your source from the Predefined sources, then enter the parameters of the source, like IP address and FQDN.

Note
During
log tapping, you can add hosts that are actively sending data to an AxoRouter instance by clicking
Register source.
-
(Optional) Add custom labels as needed.
-
Select Add.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
dell:sonicwall |
netfw |
Tested with: Dell SonicWall Add-on for Splunk technical add-on
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: SONIC_FIREWALL.
41 - Splunk
41.1 - Heavy Forwarder
Heavy Forwarder:
Receive data from Splunk.
This page describes how to configure your Splunk Heavy Forwarders to send data to AxoRouter.
Forwarding considerations
The Axoflow Forwarder Add-on works beside an existing Splunk configuration by creating an axoflow server group. Messages get cloned to the axoflow group separately during a transformation process.
The axoflow server group should not be part of the defaultGroup in the [tcpout] stanza otherwise all messages will be sent to AxoRouter twice. If the defaultGroup is not configured already, you can either:
-
Disable forwarding completely.
[tcpout]
defaultGroup = NoForward
-
Use a specific default group. For example, use default-autolb-group, as servers added through the UI will be part of it by default.
[tcpout]
defaultGroup = default-autolb-group
Prerequisites
Steps
To configure your Splunk Heavy Forwarders to send data to AxoRouter. Complete the following steps.
-
Create a new Syslog Connector rule with the following parameters:
-
Select Routers > Add Rule > Syslog > Custom
-
Enter splunk-hf into the Rule Name field.

-
Set the Router Selector so it matches the AxoRouter instances where your Splunk Heavy Forwarders will be forwarding their data. If you leave the Router Selector field empty, the rule will match all AxoRouters.
You can use any labels and metadata of the AxoRouter hosts in the Router selectors, for example, the hostname of the AxoRouter, or any custom labels.
- If you leave the Router Selector field empty, the selector will match every AxoRouter instance.
- To select only a specific AxoRouter instance, set the
name field to the name of the instance as selector. For example, name = my-axorouter.
- If you set multiple fields in the selector, the selector will match only AxoRouter instances that match all elements of the selector. (There in an AND relationship between the fields.)
-
In the Preprocessing steps section, enable Classify.

-
In the Syslog settings section:
- Select the TCP protocol.
- Select NUL terminated framing.
- Enter 9900 into the Port field.
-
Select Add.
-
Install the Axoflow Forwarder Add-on you’ve received from the Axoflow Support Team on your Splunk Heavy Forwarders.
-
Configure name resolution for the axorouter host by completing one of the following:
-
Add axorouter to the /etc/hosts file to resolve to the IP address of your AxoRouter instance where this host is sending data.
-
Alternatively, you can add the following snippet to your /opt/splunk/etc/system/local/outputs.conf file:
[tcpout:axoflow]
server = <AXOROUTER_IP1>:9900, <AXOROUTER_IP2>:9900
# configure maxQueueSize to allow for a temporary in-memory buffer if the destination is slow or unavailable
# maxQueueSize = 100MB
# configure a persistentQueueSize to allow for data to be queued on disk if the destination is slow or unavailable
# persistentQueueSize = 1GB
Note that if you set multiple AxoRouters in the server field, the forwarder will load-balance among them.
Configure either in-memory (maxQueueSize) or on-disk (persistentQueueSize) queueing to avoid data loss in case the destination is slow or unavailable.
-
Install the Axoflow Forwarder Add-on using the Splunk UI.
-
Restart splunkd.
-
Add the source to AxoConsole.
-
Open the AxoConsole and select Topology.
-
Select Add Item > Source.

-
If the source is actively sending data to an AxoRouter instance, select Detected, then select your source.
-
Otherwise, select the vendor and product corresponding to your source from the Predefined sources, then enter the parameters of the source, like IP address and FQDN.

Note
During
log tapping, you can add hosts that are actively sending data to an AxoRouter instance by clicking
Register source.
-
(Optional) Add custom labels as needed.
-
Select Add.
Classification on AxoRouter
Note that when AxoRouter receives logs from Splunk HF using the Axoflow Forwarder Add-on:
- If classification is disabled on AxoRouter, the original source, sourcetype, index, timestamp and host metadata are preserved.
- If classification is enabled, then a successful classification overrides the sourcetype and the index, while the timestamp and host are overwritten if the original message contains these more specific information.
- If you want to disable the automatic classification on AxoRouter for certain messages received from the Axoflow Forwarder Add-on, add a Condition to the Classify processing step in the related flow, so the Condition won’t match the sourcetype. For example:
meta.envelope.splunk.sourcetype != your-sourcetype
42 - Superna
42.1 - Eyeglass
Eyeglass:
Manages and automates data protection, DR, and reporting for PowerScale environments.
The following sections show you how to configure Superna Eyeglass to send their log data to Axoflow.
CAUTION:
Make sure to set data forwarding on your appliances/servers as described in this guide. Different settings like alternate message formats or ports might be valid, but can result in data loss or incorrect parsing.
Prerequisites
Steps
Note: The steps involving the Superna Eyeglass user interface are just for your convenience, for details, see the official documentation.
-
Log in to Ransomware Defender and open the Zero Trust menu.
-
Click the plus sign to add a webhook target.
-
Set the parameters of the webhook.
- Name: Enter a name for the webhook, for example,
Axoflow.
- URL: Enter the URL of the webhook connector of the AxoRouter instance where you want to post messages.
- Event Severity Filter: Select the severities of the events that you want to forward to the webhook.
- Lifecycle filter: Select the lifecycle changes that trigger a post message to the webhook.
-
Click Save, then the Test webhooks button. This will send a post message with a sample payload.
-
Add the source to AxoConsole.
-
Open the AxoConsole and select Topology.
-
Select Add Item > Source.

-
If the source is actively sending data to an AxoRouter instance, select Detected, then select your source.
-
Otherwise, select the vendor and product corresponding to your source from the Predefined sources, then enter the parameters of the source, like IP address and FQDN.

Note
During
log tapping, you can add hosts that are actively sending data to an AxoRouter instance by clicking
Register source.
-
(Optional) Add custom labels as needed.
-
Select Add.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
superna:eyeglass |
main |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: SUPERNA_EYEGLASS.
43 - syslog-ng
By default, Axoflow treats syslog-ng sources as a generic syslog source.
- The easiest way to send data from syslog-ng to Axoflow is to configure it to send data to an AxoRouter instance using the syslog protocol.
- If you’re using syslog-ng Open Source Edition version 4.4 or newer, use the
syslog-ng-otlp() driver to send data to AxoRouter using the OpenTelemetry Protocol.
Note that even if syslog-ng is acting as a relay (receiving data from other clients and forwarding them to AxoRouter), on the Topology page it will be displayed as a data source.
Prerequisites
44 - Thales
44.1 - Vormetric Data Security Platform
Vormetric Data Security Platform:
Provides data encryption, key management, and access controls across cloud and on-premise environments.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
thales:vormetric |
netauth |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: VORMETRIC.
45 - Trellix
45.1 - Central Management System (CMS)
Central Management System (CMS):
Centralized policy and configuration management platform for Trellix security products.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
trellix:cms |
trellix:cms |
netops |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FIREEYE_CMS.
45.2 - Email Threat Prevention (ETP)
Email Threat Prevention (ETP):
Analyzes and filters email traffic to block phishing, malware, and targeted email-based threats.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
fe_etp |
fireeye |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FIREEYE_ETP.
45.3 - Endpoint Security (HX)
Endpoint Security (HX):
Detects and responds to advanced threats on endpoints using behavior-based analysis and threat intel.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Note that the device can be configured to send logs formatted as JSON or CEF. AxoRouter can automatically parse all flavors.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
hx_json |
fireeye |
fe_json |
fireeye |
hx_cef_syslog |
fireeye |
Tested with: FireEye Add-on for Splunk Enterprise
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FIREEYE_HX.
Earlier name/vendor
FireEye Endpoint Security (HX)
45.4 - ePolicy Orchestrator (EPO)
ePolicy Orchestrator (EPO):
Analyzes and filters email traffic to block phishing, malware, and targeted email-based threats.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
source |
mcafee:epo:syslog |
epav |
trellix_endpoint_security |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: MCAFEE_EPO.
Earlier name/vendor
McAfee ePolicy Ochestrator (EPO)
45.5 - MPS
MPS:
Appliance for detecting and blocking advanced threats through inline malware inspection.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
source |
index |
trellix:mps |
trellix:mps |
netops |
46 - Trend Micro
46.1 - Deep Security Agent
Deep Security Agent:
Provides anti-malware, intrusion prevention, and log inspection for cloud and on-prem servers.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
deepsecurity |
epintel |
deepsecurity-system_events |
epintel |
deepsecurity-intrusion_prevention |
epintel |
deepsecurity-firewall |
epintel |
deepsecurity-antimalware |
epintel |
deepsecurity-integrity_monitoring |
epintel |
deepsecurity-log_inspection |
epintel |
deepsecurity-web_reputation |
epintel |
deepsecurity-app_control |
epintel |
deepsecurity-system_events |
epintel |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: TRENDMICRO_DEEP_SECURITY.
47 - Ubiquiti
47.1 - Unifi
Unifi:
Manages network devices including routers, switches, and access points with centralized control.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
ubnt |
netops |
ubnt:cef |
netops |
ubnt:dhcp |
netops |
ubnt:dnsmasq |
netops |
ubnt:edgeswitch |
netops |
ubnt:hostapd |
netops |
ubnt:link |
netops |
ubnt:mcad |
netops |
ubnt:sudo |
netops |
ubnt:wireless |
netops |
ubnt:fw |
netfw |
ubnt:fw:cef |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: UBIQUITI_SWITCH.
48 - Varonis
48.1 - DatAdvantage
DatAdvantage:
Monitors data access and permissions to detect insider threats and automate compliance reporting.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
varonis:ta |
main |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: VARONIS.
49 - Vectra AI
Earlier name/vendor
Vectra Cognito
49.1 - X-Series
X-Series:
Detects and investigates cyberattacks across cloud, data center, and enterprise networks using AI.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
vectra:cognito:detect |
main |
vectra:cognito:accountdetect |
main |
vectra:cognito:accountscoring |
main |
vectra:cognito:audit |
main |
vectra:cognito:campaigns |
main |
vectra:cognito:health |
main |
vectra:cognito:hostscoring |
main |
vectra:cognito:accountlockdown |
main |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: VECTRA_DETECT.
50 - Zscaler appliances
50.1 - Zscaler Nanolog Streaming Service
Zscaler Nanolog Streaming Service:
Cloud-based secure internet gateway that inspects traffic for threats and enforces policies.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
zscalernss-alerts |
netops |
zscalernss-tunnel |
netops |
zscalernss-web |
netproxy |
zscalernss-web:leef |
netproxy |
Tested with: Zscaler Technical Add-On for Splunk
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: ZSCALER_INTERNET_ACCESS.
50.2 - Zscaler Log Streaming Service
Zscaler Log Streaming Service:
Provides secure remote access to internal apps without exposing them to the public internet.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
You can use the labels as:
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype |
index |
zscalerlss-zpa-app |
netproxy |
zscalerlss-zpa-audit |
netproxy |
zscalerlss-zpa-auth |
netproxy |
zscalerlss-zpa-bba |
netproxy |
zscalerlss-zpa-connector |
netproxy |
Tested with: Zscaler Technical Add-On for Splunk
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: ZSCALER_ZPA, ZSCALER_ZPA_AUDIT.












