This is the multi-page printable view of this section. Click here to print.
Fortinet
- 1: FortiGate firewalls
- 2: FortiMail
- 3: FortiProxy
- 4: FortiWeb
1 - FortiGate firewalls
FortiGate firewalls: Enterprise firewall platform offering threat protection, VPN, and traffic filtering for secure networking.
The following sections show you how to configure FortiGate Next-Generation Firewall (NGFW) to send their log data to Axoflow.
CAUTION:
Make sure to set data forwarding on your appliances/servers as described in this guide. Different settings like alternate message formats or ports might be valid, but can result in data loss or incorrect parsing.Prerequisites
- You have administrative access to the firewall.
- The date, time, and time zone are correctly set on the firewall.
- You have an AxoRouter deployed and configured with a Syslog connector that has parsing and classification enabled (by default, every AxoRouter has such connectors). This device is going to receive the data from the firewall.
-
You know the IP address the AxoRouter. To find it:
- Open the AxoConsole.
- Select the Routers or the Topology page.
- Select on AxoRouter instance that is going to receive the logs.
- Check the Networks > Address field.
Steps
Note: The steps involving the FortiGate user interface are just for your convenience, for details, see the official FortiGate documentation.
-
Log in to your FortiGate device. You need administrator privileges to perform the configuration.
-
Register the address of your AxoRouter as an Address Object.
-
Select Log & Report > Log Settings > Global Settings.
-
Configure the following settings:
- Event Logging: Click All.
- Local traffic logging: Click All.
- Syslog logging: Enable this option.
- IP address/FQDN: Enter the address of your AxoRouter:
%axorouter-ip%
-
Click Apply.
-
-
Add the source to AxoConsole.
-
Open the AxoConsole and select Topology.
-
Select Add Item > Source.
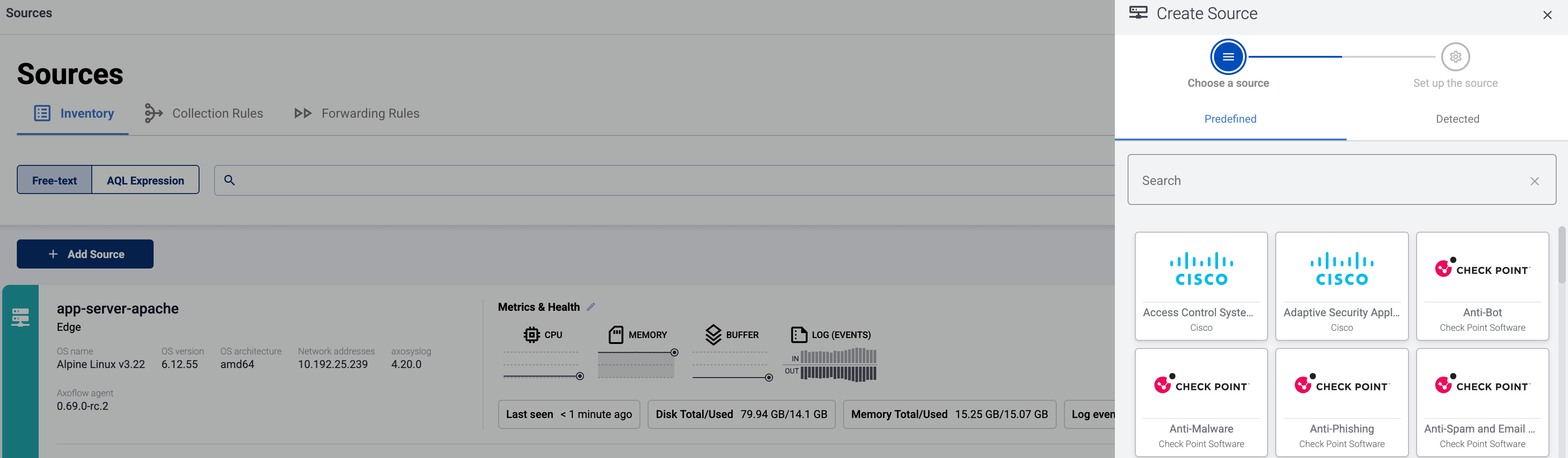
-
If the source is actively sending data to an AxoRouter instance, select Detected, then select your source.
-
Otherwise, select the vendor and product corresponding to your source from the Predefined sources, then enter the parameters of the source, like IP address and FQDN.
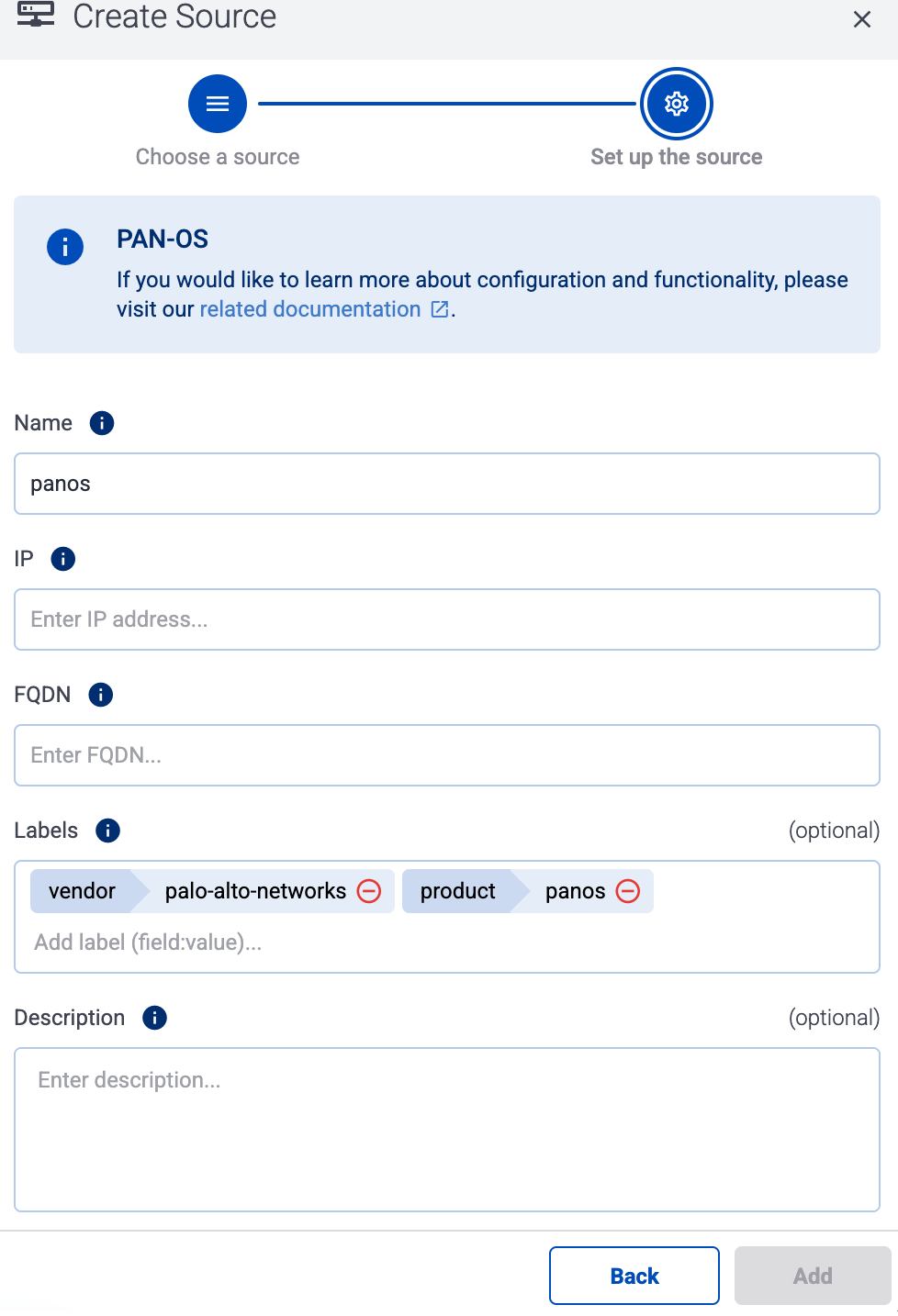
Note During log tapping, you can add hosts that are actively sending data to an AxoRouter instance by clicking Register source. -
-
(Optional) Add custom labels as needed.
-
Select Add.
-
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label | Message field | value |
|---|---|---|
vendor |
meta.vendor |
fortinet |
product |
meta.product |
fortigate |
service |
meta.service.name |
fortigate |
You can use the labels as:
- Filter labels on the Analytics page,
- in the Filter By Label field during log tapping.
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype | index |
|---|---|
fortigate_event |
netops |
fortigate_traffic |
netfw |
fortigate_utm |
netfw |
Tested with: Fortinet FortiGate Add-On for Splunk technical add-on
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORTINET_FIREWALL.
2 - FortiMail
FortiMail: Secures inbound and outbound email with spam filtering, malware protection, and advanced threat detection.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label | Message field | value |
|---|---|---|
vendor |
meta.vendor |
fortinet |
product |
meta.product |
fortimail |
service |
meta.service.name |
fortiweb |
You can use the labels as:
- Filter labels on the Analytics page,
- in the Filter By Label field during log tapping.
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype | index |
|---|---|
fml:log |
email |
Tested with: FortiMail Add-on for Splunk technical add-on
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORTINET_FORTIMAIL.
3 - FortiProxy
FortiProxy: Protects from internet threats like malware, phishing, and data loss by inspecting web traffic, filtering content, controlling applications, and enforcing security policies
To send logs from FortiProxy to AxoRouter, configure remote logging to a syslog server on FortiProxy. Use the IP address of AxoRouter as the syslog server IP address. Set FortiProxy to send logs in the default format. (If you need to send the logs in CEF format, contact our support team). For details, see Generic tips.
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label | Message field | value |
|---|---|---|
vendor |
meta.vendor |
fortinet |
product |
meta.product |
fortiproxy |
service |
meta.service.name |
fortigate |
You can use the labels as:
- Filter labels on the Analytics page,
- in the Filter By Label field during log tapping.
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype | index |
|---|---|
fortiproxy_anomaly |
netfw |
fortiproxy_event |
netops |
fortiproxy_traffic |
netfw |
fortiproxy_utm |
netfw |
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORTINET_WEBPROXY.
4 - FortiWeb
FortiWeb: Web application firewall protecting websites from attacks like XSS, SQL injection, and bot threats.
To onboard such a source to Axoflow, complete the generic appliance onboarding steps.
Labels
Axoflow automatically adds the following labels to data collected from this source:
| Analytics label | Message field | value |
|---|---|---|
vendor |
meta.vendor |
fortinet |
product |
meta.product |
fortiweb |
service |
meta.service.name |
fortiweb |
You can use the labels as:
- Filter labels on the Analytics page,
- in the Filter By Label field during log tapping.
You can use the message fields
- in Flow Processing steps, for example, in the Query field of Select Messages steps,
- in AQL expressions in the search bars.
Sending data to Splunk
When sending the data collected from this source to Splunk, Axoflow uses the following sourcetype and index settings:
| sourcetype | index |
|---|---|
fwb_log |
netops |
fwb_attack |
netids |
fwb_event |
netops |
fwb_traffic |
netfw |
Tested with: Fortinet FortiWeb Add-0n for Splunk technical add-on
Sending data to Google SecOps
When sending the data collected from this source to a dynamic Google SecOps destination, Axoflow sets the following log type: FORTINET_FORTIWEB.